DDoS Revisited (Bio-Zombie)

About 10 years ago my first blog post was about DDoS attacks - the reason behind this was because my first few websites were victims to it. Childhood DDoS attacks were just a collection of infected hosts flooding HTTP requests to my server. Now with 10 years more knowledge - we are going to dive into DDoS attacks again.
Everything in this post about my experience is 10+ years old all from memory. I do NOT do this stuff anymore.
My introduction to DDoS attacks was from booting people from games of Halo in order to win. This was the childish me, opting instead of the right path, I went down a dark path becoming a type of kid I am not happy I was.
I started asking around and met a few folks who hooked me up with tools. The idea of them was simple: create a malicious file and spread it over torrents. Once you infected enough hosts you could leverage those machines to overload your intended victim.
Looking back at this a decade later, I realized how much of a pawn in a larger system I was. Infected hosts need to communicate back to something so they show up in this tool. This is known as a CnC (Command and Control) host. This is the control machine or host the infected binary communicates back with in order to register itself.
Those CnC machines are normally blocked or sink-holed at a global network level once law enforcement becomes aware. This leads creative hackers to run their bots from social networks like Twitter posts and Pastebin, because what ISP or network is going to globally block those websites?
This makes sense to me now, because even with my computer offline my infected binaries I spread among torrents would still increase my host count whenever I returned to the application.
My guess is that the author I obtained this from owned a "master" binary and build. This would have control over all infected hosts, but could produce "child" binaries. The child binaries would be passed to chumps like myself and I did the dirty work. Spreading malware to the world to boost my own infected count, unaware I was probably growing the host count of the mastermind.
The booting tool supported the following types of DDoS attacks:
- UDP Flood
- HTTP Flood
- Ping Flood
- Custom Port Flood
These are nothing special, which would just abuse the amount of infected hosts towards one target on the specified port.
So with a large enough army of infected hosts, the next step was the simple part. Proxy your Xbox connection through your computer, identify through multiple matches the IPs that never change and play with your friends. That left you 4 IPs you didn't know. Target your bots towards one of those IPs, lag them enough for the game to kick them. Win the game against an outnumbered team. Disgusting but effective.
Moving on from that, the tools I used upgraded with time.
With success in spreading malware, I got "upgraded" to custom labeled applications and smarter malware which was less detectable. However, my method of spreading was still laughable. I would just make torrents named after movies in theaters with an exe as the download. It amazed me how many people downloaded and clicked it.
One thing that started around this time was the idea of amplification DDoS attacks. Some creative people noticed that instead of just leveraging infected hosts, why not make a spoofed DNS request from the infected host to a legitimate open DNS server. Inside the spoofed request would be a return IP of the intended victim.
This would produce the following jump
- CnC -> Infected Host -> Open DNS Server -> Reflected to Target
Breaking down the words "reflection" and "amplification" we can understand how DDoS attacks evolved.
- Reflection - The reply of a request going to a spoofed origin.
- Amplification - The reply larger than the request.
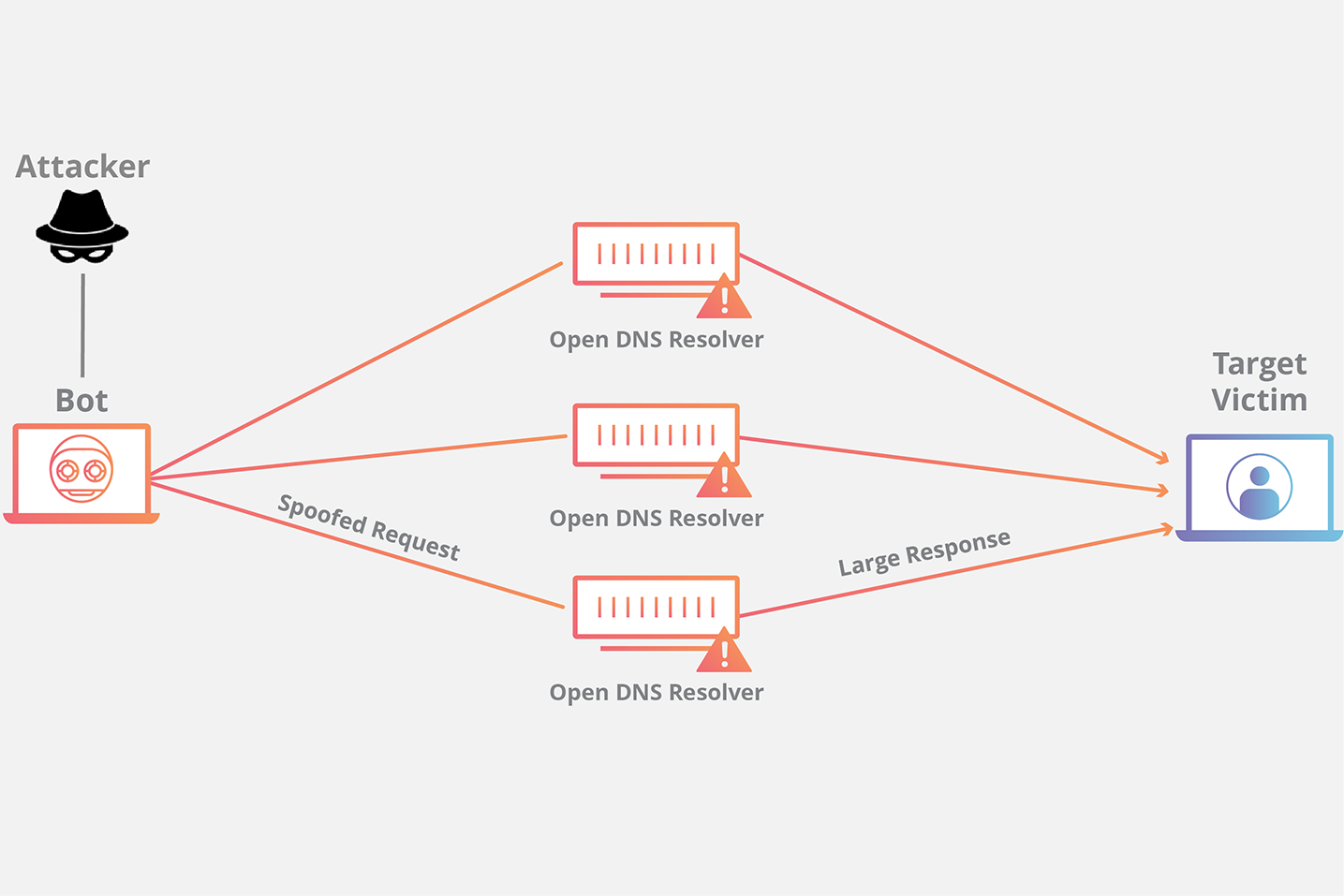
Cloudflare does a good job making an image for this example for one infected host sending multiple spoofed DNS requests. You can see how easily it is to make this a massive attack. More infected hosts or more open DNS resolvers can make this a deadly attack.
Paired with the amplification factor, it could be even deadlier. Imagine a web request you send to a DNS server of roughly 60 bytes. However, you ask the DNS server to respond with the largest payload it has to your victim. This would generate probably over 4000 bytes in response. So you can see how much more data the victim would receive.
With the abuse of DNS amplification, web-server administrators globally began patching to prevent the abuse. However, DNS was just one medium for reflection. Soon it was NTP, SNMP, then memcached. The list is never ending and the attacks will only continue to evolve.
I hope this part story and part knowledge can help bring more information to the ever expanding landscape of DDoS attacks.
