Safety in Patterns

A few weeks ago as I arrived at the park to workout and do my morning stretches I saw a regular who seems to be there every weekend like me. They asked where I've been since I wasn't there the prior week as I was up in West Virginia.
I explained a simple phrase of "out of town" and that was that. What I found interesting is that if someone can notice my pattern was broken - it seems you build up quite an amount of safety in that. Now I doubt any of these park goers would treat me missing from a normal workout as anything to be alarmed about, but interesting enough that they noticed.
It seems this notion of finding anomalies within a pattern is the strength of many many systems. Whether its a network defense system looking for out of the norm packets or a credit card company noticing where and what you normally buy.
Let's take a look at nzyme v2.0 and how it operates among patterns.
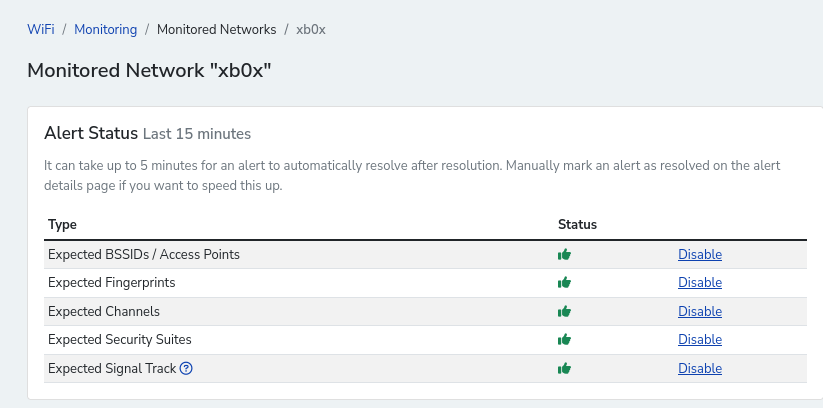
You can see above that nzyme will detect differences to a trusted network by quite a lot of methods, but what I want to lock into is the "Expected Signal Track". Given a static position of your nzyme hardware - it would develop a consistent track of the signal strength of the monitored networks.
This of course assumes that your access points and nzyme hardware is stationary. This ends up building a waterfall chart of the signal strength as packets go across the air.
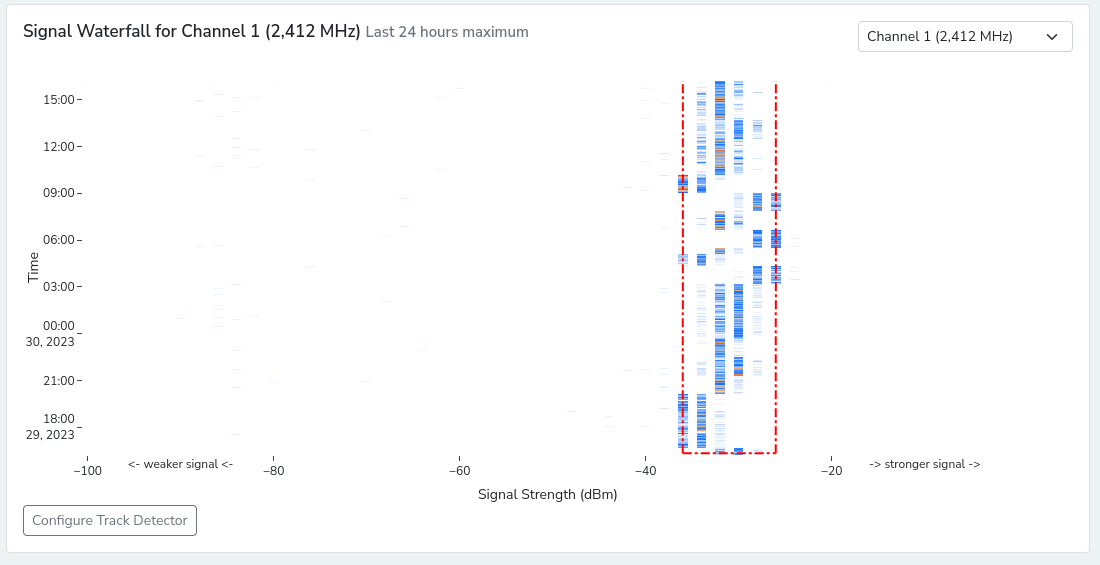
This becomes quite possibly the best protection against spoofed/fake networks in my personal opinion. When a malicious network comes online chances are it isn't on the same hardware or area as trusted devices.
This means that near instantly when an attacker launches a malicious network nzyme would notice a different pattern to signal strength and immediately alert. This method wouldn't work for a brand new stood up network to immediately flag malicious activity, but it's seeming that some of the best detection is a break to a pattern.
Take my credit card and what happened with Akamai acquiring Linode (which I'm not happy about).
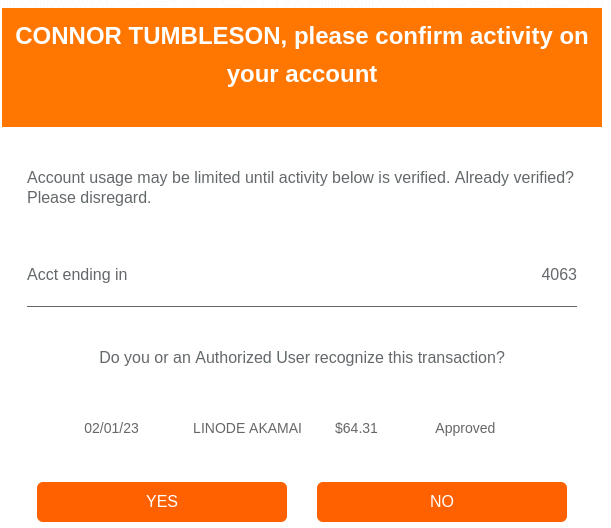
Once Akamai took over billing - the name (and price) started changing. This threw off some patterns on my credit card and I had to confirm the transaction.
It seems that credit card companies probably have entire departments dedicated to anti-fraud with huge amounts of logic or AI to shift through transactions to look for oddities to a pattern.
The more I think the more things appear to be based on anomalies to patterns. Even to the extreme that some pattern watching becomes profiling - all in all some interesting things to think about.
