The Weaponized Process

A few months ago at a local conference I ran into some folks that work at a pretty big national technology company. One of the things we discussed was the rise of "sim swap" attacks, which basically boils down to social engineering an individual to perform a task they should not do.
If you take that specific example - at times a sim swap is the only valid path to move a phone number, which will require a good deal of personal information to validate and confirm. Attackers have gotten pretty good due to the vast amount of information leaks to gather all the information needed to perform a swap.
At that point you then run into the processes and procedures in place at each respective phone company. If you roll the clock back a lot - it was almost as easy as just rolling the dice with who answered the phone. Chances are you might get someone willing to grant your sim request as you sell a story.
In more modern times - features have been released by the respective companies in order to thwart this type of attack. They've even begun delaying processes in order to give a chance in a malicious situation for the victim to respond.
XXX: A SIM change has been requested for this line. Reply with 1 to Approve this change or 2 to Decline. If we do not hear a response from you within 10 minutes, the change will proceed as requested.
What I find extremely interesting is that every process or support avenue begins for the right reasons, but is almost immediately tested for how it can be abused.
Take for example like YouTube or Twitch which launched a major immediate and direct route in order to combat copyright infringement. In theory this seemed like a good idea where companies could shut down obvious movie uploads or any other purely malicious content.
However, what happened was very quickly people realized you could destroy a person's YouTube Channel with some quick claims about infringement. To make matters worse is YouTube wouldn't mediate these claims, so if a disagreement occurred it would be between the party and victim to resolve it.
Of course that didn't take too long for bogus requests to be thrown from shell companies or individuals to demolish competitor channels. YouTube reacted and then provided some methods for a legal response to fight back a claim. However, sometimes all you need to do is start a copyright claim as that is instant - the appeal and resolution may take weeks to months and by that point - the damage is done.
Now if you look at Ingress, a game I've been playing for 10+ years - they've had their own share of oddities.
In the beginning if you wanted to submit a new portal (Point of Interest) you would email an address and wait days to months for someone to approve/deny it. As Ingress evolved they added the ability to submit new locations directly into the application - this helped collect all the metadata they needed instead of the manual email route.
This created such a huge influx of submissions that it became clear that Niantic itself couldn't process the entire world's submission of POIs, so they disabled submissions. This was quite sad as it seemed the growing world of Ingress would halt. Roughly a year later a program called Operation Portal Recon (OPR) launched which allowed the players themselves to judge the quality of incoming submissions.
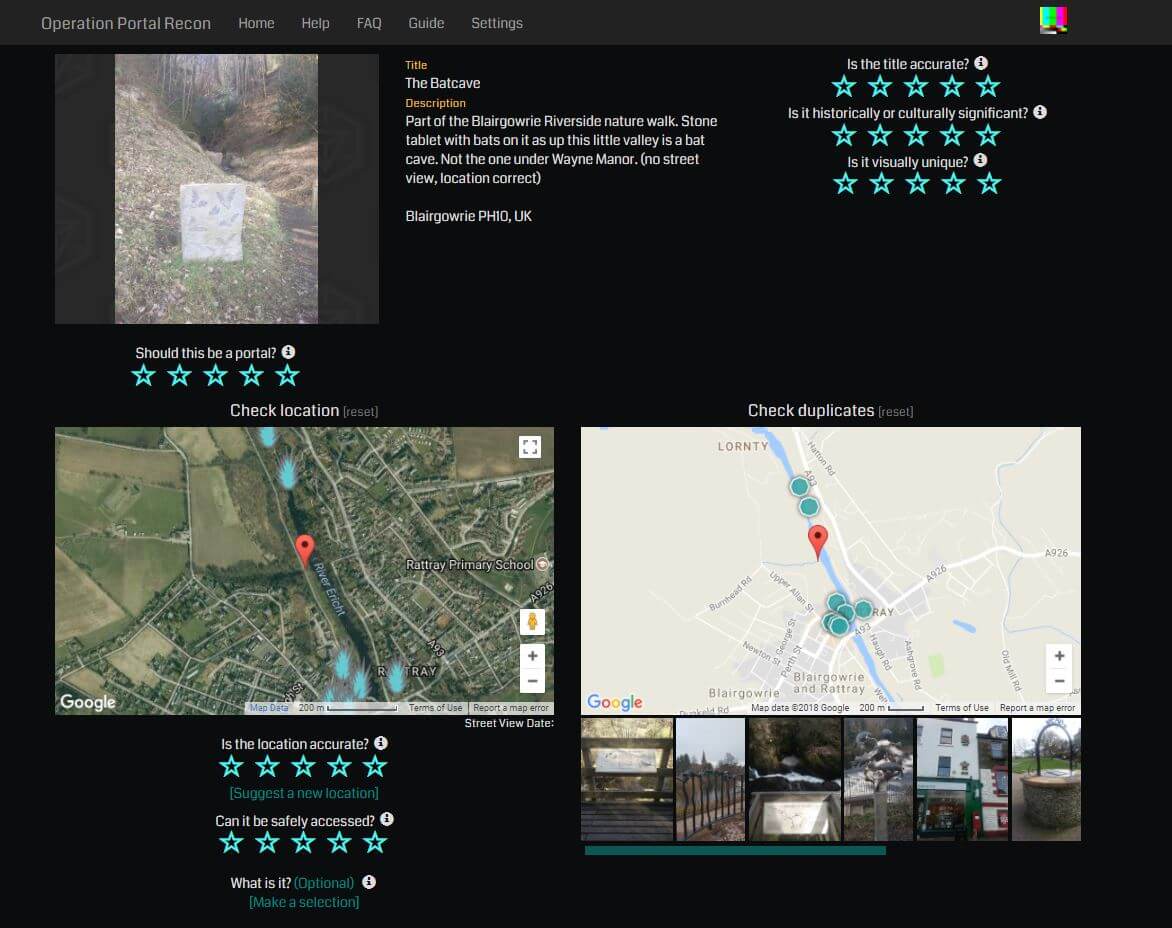
As shown above a user would quickly grade a portal on a variety of things in order to qualify or reject a submission. Of course this didn't take long for the first form of abuse to occur. Since it was user-generated content, some folks quickly developed patterns to detect their own submissions between the two teams.
It may be a trailing comma or leading space, but each team knew that meant their team submitted it. This would lead to rejections that were valid and submissions that were not.
All for the play of getting portals into areas they shouldn't be. Whether this was a private business location or personal property - it became weaponized.
As OPR features grew the other game under Niantic (Pokemon Go) was itching to take part in this process. They wanted to change the POIs for different reasons - while Ingress was about exploring and finding difficult to reach portals, Pokemon players generally just wanted a huge amount of Wayspots everywhere.
So a few years later OPR was no more - it was shutdown and evolved into Niantic Wayfarer for a cross-game database of locations (now known as Wayspots).
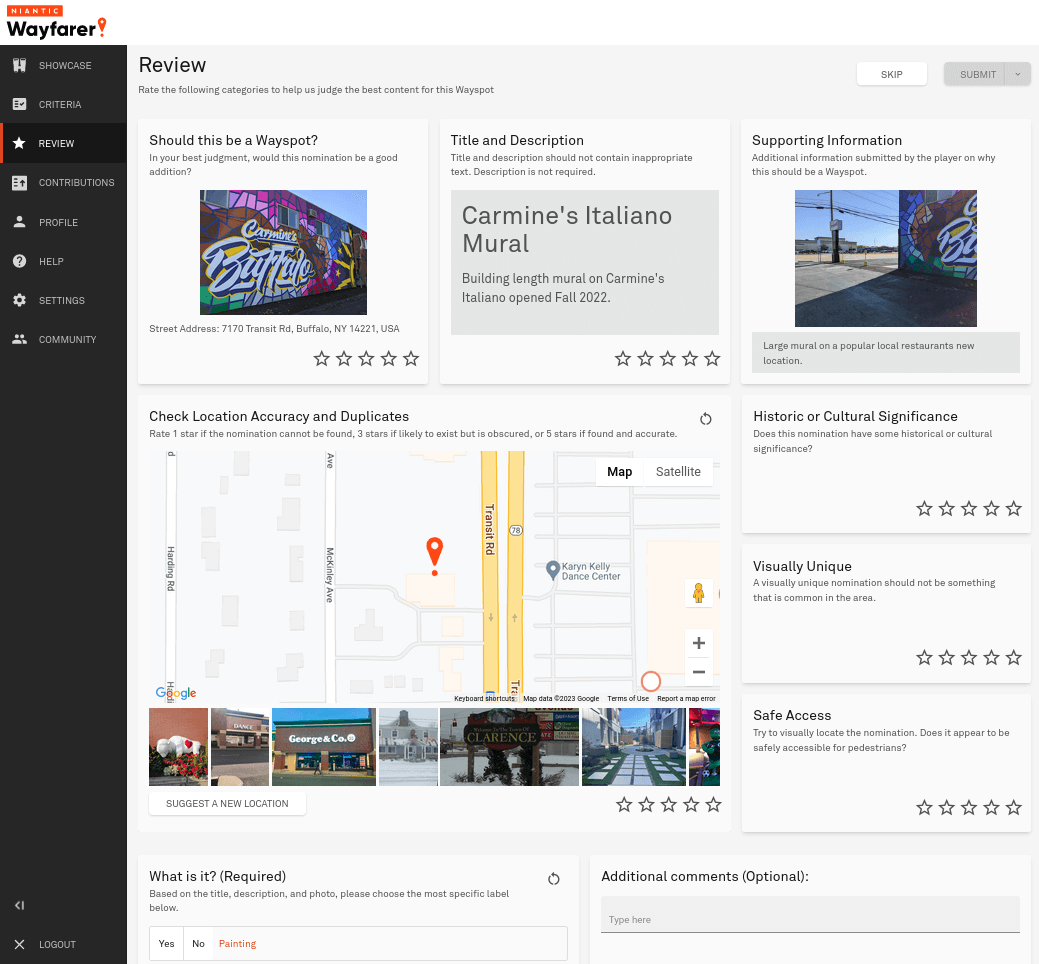
Sure enough abuse was back - this time with edits causing all the in-game links and fields to drop. Was it being moved to correct an inaccuracy of a few meters or being moved to impact the game board?
The case was clear that in most situations - no one cared if the Wayspot was a few meters misplaced - they just wanted to do the damage when a point moved. Niantic took a bit, but responded again to this new form of abuse and prevented moved locations from adapting the game board.
Time and time again in Ingress every new pattern was abused and it becomes a toxic pool of thinking. You either join in the abuse in a form of revenge or take the high road and hope people just play the game.
Abuse doesn't always have to be malicious though - think about GitHub support who has mentioned that a large amount of support requests they get are people emailing support about an issue in a repository. It seems crazy to me that just because some people can't install/build React Native they think an avenue for solving that is emailing GitHub itself.
So all in all - malicious or not if you add a process it'll be weaponized or abused.
