The Cicada 3301 Mystery (Puzzle 3 Solve) - Part 4

We pick up where we left off in the January 2014 puzzle - this is Part 4.
We ended the last part after a long process of discovering a book & associated book code from a collection of compressed nested images within another image. Once done with that we landed on a new onion (ut3qtzbrvs7dtvzp.onion) which gave us a rather large output of hexadecimal characters.
<!--761-->
ffd8ffe000104a46494600010100000100010000ffdb0043000806060706
05080707070909080a0c140d0c0b0b0c1912130f141d1a1f1e1d1a1c1c20
242e2720222c231c1c2837292c30313434341f27393d38323c2e333432ff
// snippedWhat was odd about this page is we didn't see the common 512 character tiny string prior to this one. Either way - we know what to do at this point. Lets dump the hexadecimal characters - convert to binary and run binwalk.
➜ xxd -p -r file.hex file.bin
➜ binwalk file.bin
DECIMAL HEXADECIMAL DESCRIPTION
-----------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
754662 0xB83E6 JPEG image data, JFIF standard 1.01
1467395 0x166403 JPEG image data, JFIF standard 1.01
2170823 0x211FC7 JPEG image data, JFIF standard 1.01
This seems a bit too easy - there appears to be 4 images in sequential order. With all the confusion we've had in prior puzzles with backward images, reversed images, etc I expected something a bit more complex.
If we were to visualize this packed data - it would resemble this image.
I've recently started appreciating foremost as a tool (over binwalk) recently, so we can ask foremost to extract these 4 images.
➜ foremost file.bin
Processing: file.bin
|*|Now it appears we have 4 more pages of this Liber Primus book extracted.
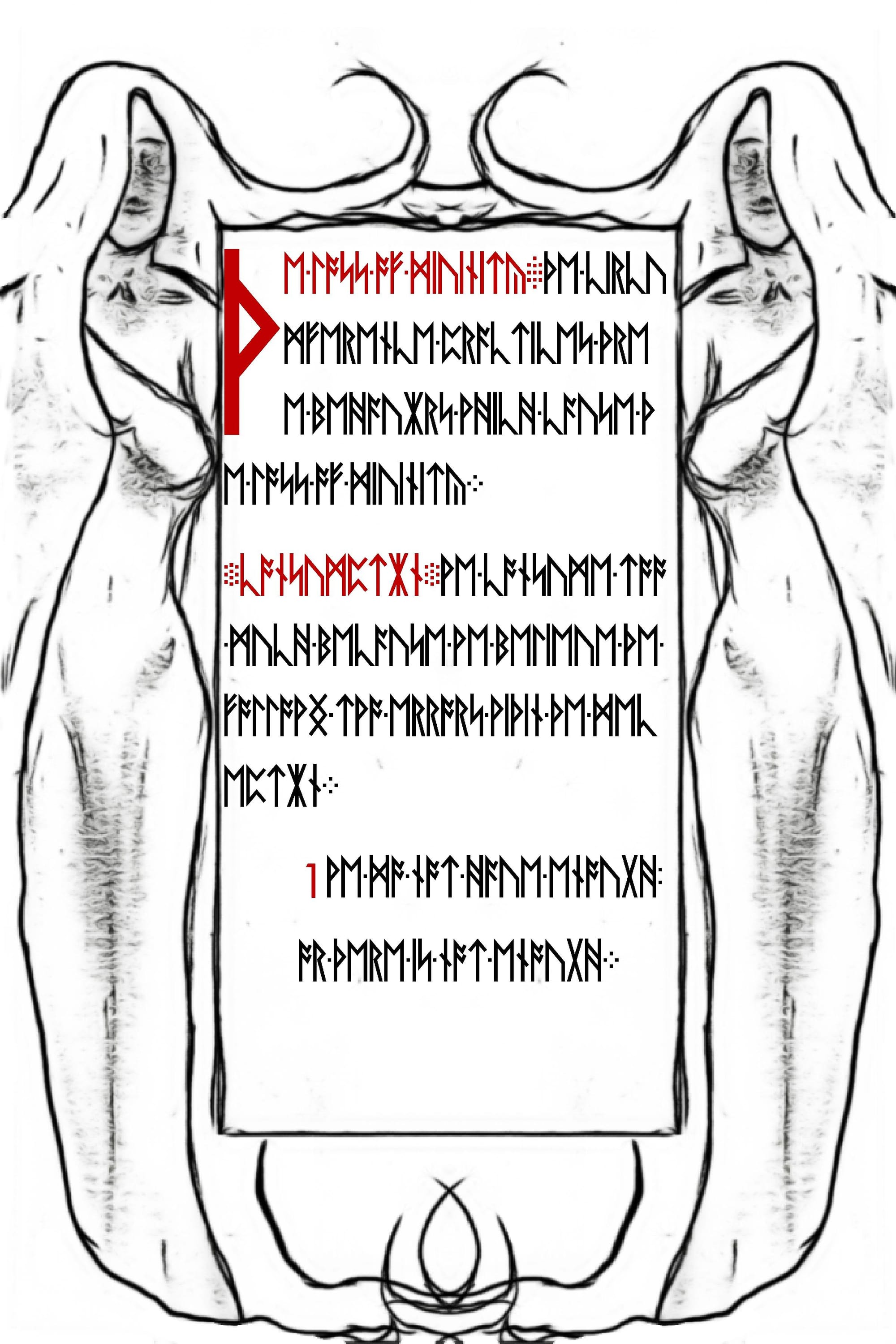

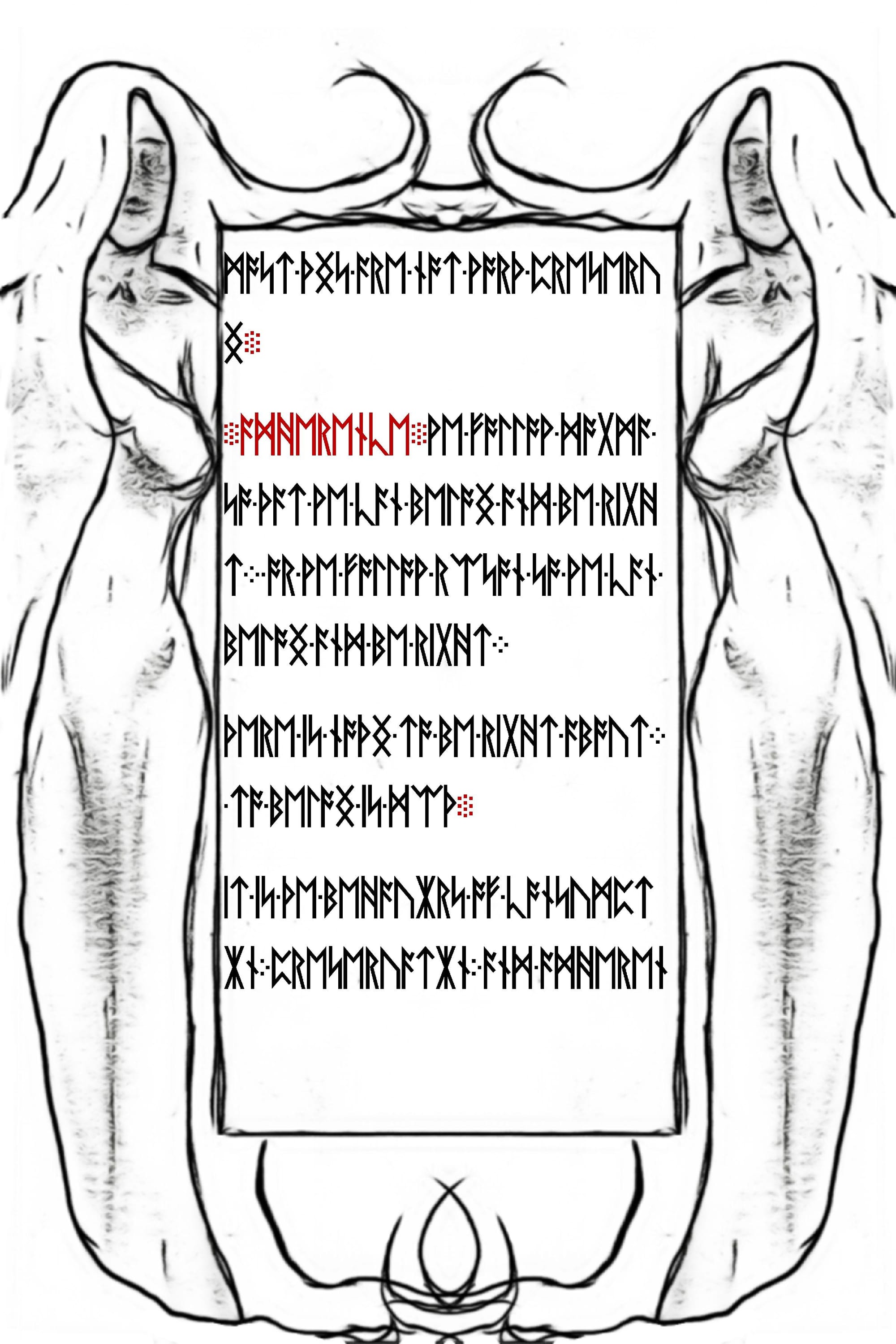
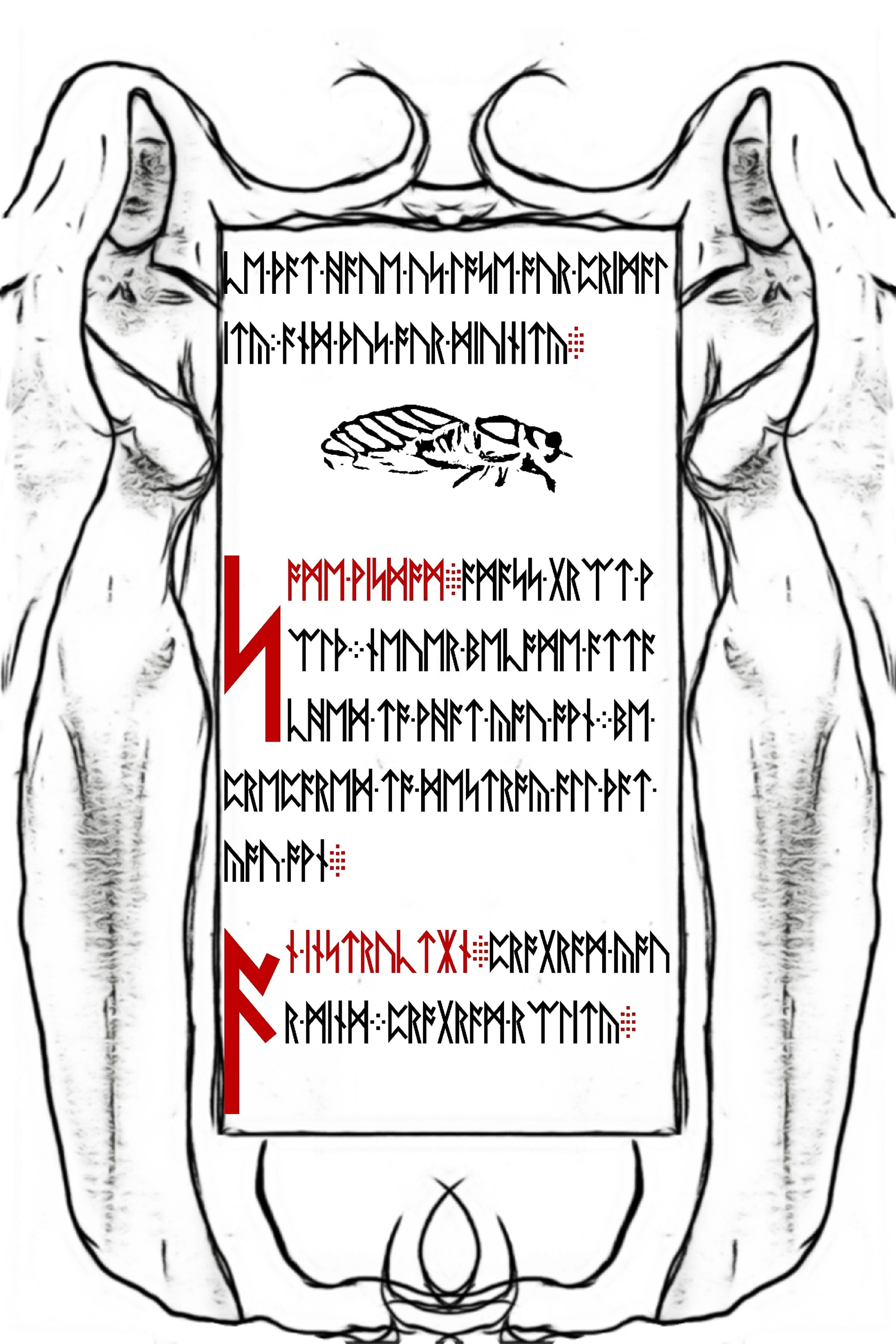
Of course we should immediately run outguess over these 4 new images to see if we find anything.
➜ for file in *.jpg; do outguess -r $file $file.out; done;
Reading 10.jpg....
Extracting usable bits: 677059 bits
Steg retrieve: seed: 99, len: 1234
Reading 11.jpg....
Extracting usable bits: 627884 bits
Steg retrieve: seed: 166, len: 1234
Reading 12.jpg....
Extracting usable bits: 623058 bits
Steg retrieve: seed: 150, len: 1234
Reading 13.jpg....
Extracting usable bits: 1433292 bits
Steg retrieve: seed: 129, len: 1234Sure enough all 4 decoded messages have some variation of this new challenge.
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
Create one Tor hidden service that can accept CGI file uploads.
When this hidden service returns and can accept input, post the
three magic squares and the URL to your Tor hidden service here.
Work alone.
3333333333333333
310 12 103
3 3
312 14 123
3 3
310 12 103
3333333333333333
Good luck.
3301So before we go refresh on our magic squares from previous puzzles - we should go figure out what these 4 pages of the book say. We have quite a collection of scripts to run on runes now - so we will try each of the following and look for a successful decoding.
- Direct Translation
- Reversed Translation
- XOR with Puzzle 2
- Brute-force Vigenère Key
- Brute-force Column Key
As we go down the list - it doesn't take long as this is a direct translation of runes to English.
ᚦᛖ ᛚᚩᛋᛋ ᚩᚠ ᛞᛁᚢᛁᚾᛁᛏᚣ --> THE LO[S|Z][S|Z] OF DIUINITYAs you can see a direct translation started spelling out "The loss of divinity". Now we have to remind ourselves of why this translation looks a bit odd.
- The
ᛋrune has either S or Z as a valid letter value. - The letter
vhas no corresponding rune.
Remember in Part 1 the book called out
DO NOT EDIT OR CHANGE THIS BOOK
OR THE MESSAGE CONTAINED WITHIN
EITHER THE WORDS OR THEIR NUMBERS
FOR ALL IS SACRED
So as we go forward we probably have to treat the messages exactly as they are decoded even if it doesn't look exactly like perfect English. As we continue going through these 4 pages they all are a simple direct translation which ends up forming a story titled "The Loss of Divinity" which we will correct into proper spelling for the sake of reading it.
The Loss of Divinity (Full)
A Loss of Divinity
The Circumference practices three behaviors which cause the loss of divinity
Consumption
We consume too much because we believe the following two errors within the deception:
- We do not have enough or there is not enough
- We have what we have now by luck
and we will not be strong enough later to obtain what we need.
Most things are not worth consuming.
Preservation
We preserve things because we believe we are weak.
If we lose them, we will not be strong enough to gain them again.
This is the deception.
Most things are not worth preserving.
Adherence
We follow dogma so that we can belong and be right
or we follow reason so we can belong and be right.
There is nothing to be right about
to belong is death
it is the behaviors of consumption
Preservation and Adherence that have us lose our Primality
and thus our Divinity
Some wisdom
Amass great wealth
Never become attached to what you own
Be prepared to destroy all that you own
An instruction
Program your mind
Program reality
Source - GitHub (A Loss of Divinity Page 10-13)
Now remember we don't have a letter V in the translation, so the proper spelling would be "Diuinity" which may or may not become relevant.
While we discovered the meaning behind those 4 pages - the onion we originally obtained those images from updated. This had become a pattern at this point where an onion was discovered, would go offline for 5-7 days and come back online changed.
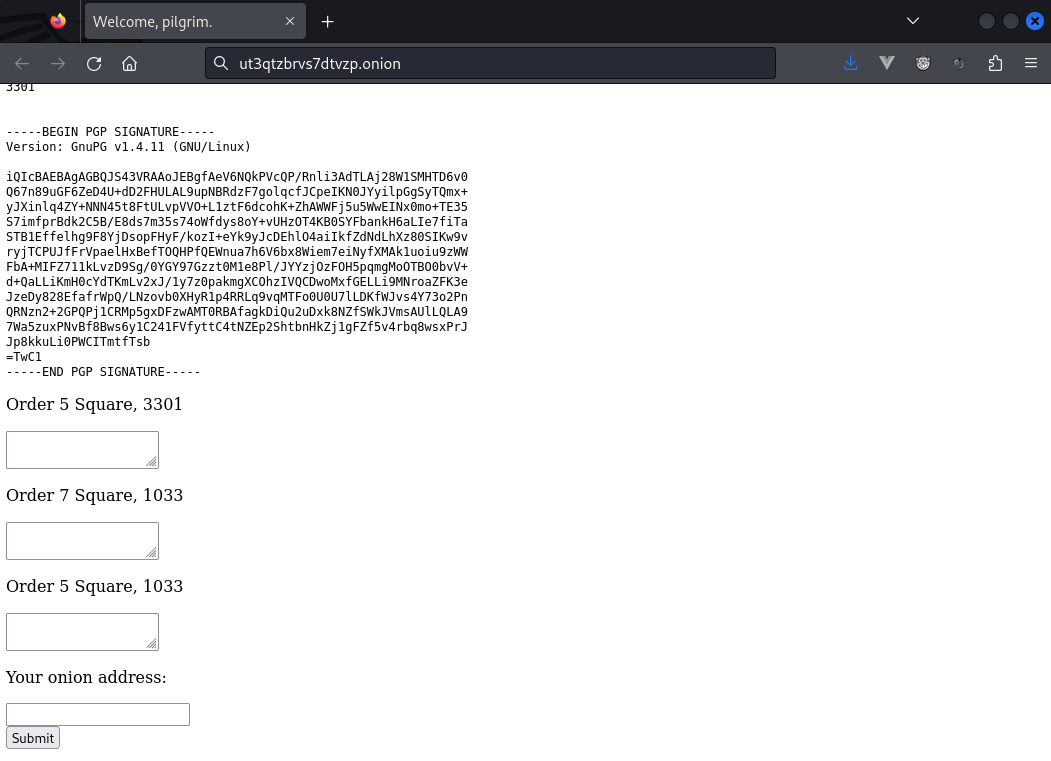
The website had a few instructions attached.
Please paste the magic squares into the appropriate textareas below, then
provide the URL to your Tor hidden service.
The path to your CGI script which accepts uploads should be '/cgi-bin/upload' and the HTML form input which accepts file uploads should be named 'file'.
Additionally, please generate a GnuPG key pair, and place the public key
in the location '/key.asc'.
So there is a lot going on here we have to breakdown.
- We have to generate 3 different magic squares with values 1033 (twice) and 3301 at either a 7x7 or 5x5 grid. Thankfully I recently blogged about magic squares and our previous weird images from Part 3 had some numbers hidden, which may be related.
- We have to host & build a Tor website that supports file uploads (under name
file) at the location of/cgi-bin/upload.- Additionally serving our respective public key at
/key.asc
- Additionally serving our respective public key at
Starting with the magic squares - we have to make/find each of the following:
- A 5x5 magic square of value 3301.
- A 7x7 magic square of value 1103.
- A 5x5 magic square of value 1103.
So the question is whether we have to painfully generate these or discover them within the previous puzzles. We know way back in Part 2 (Puzzle 3) we found a magic square that was utilized for decoding a page of the book (Page 5).
272 138 341 131 151
366 199 130 320 18
226 245 91 245 226
18 320 130 199 366
151 131 341 138 272magic square from Part 2 - Puzzle 3.
This is a perfectly valid magic square that sums to 1103 on every row/column/diagonal. So I'm leaning towards going back through all media/assets from the previous puzzles to discover more squares. We know from Part 3 that some numbers were hidden in the portrait, but we gave up fully understanding what numbers.
Thankfully with a few weeks between blog posts - a bit of renewed energy to try again and it didn't take long. I just popped the image into Forensically Beta and messed with the JPEG error/correction scale. Once I started seeing the cicada logo and person (Rasputin?) come into focus, I just messed with the sliders until numbers appeared.

This resulted in an image that was quite readable with numbers on left and right side.
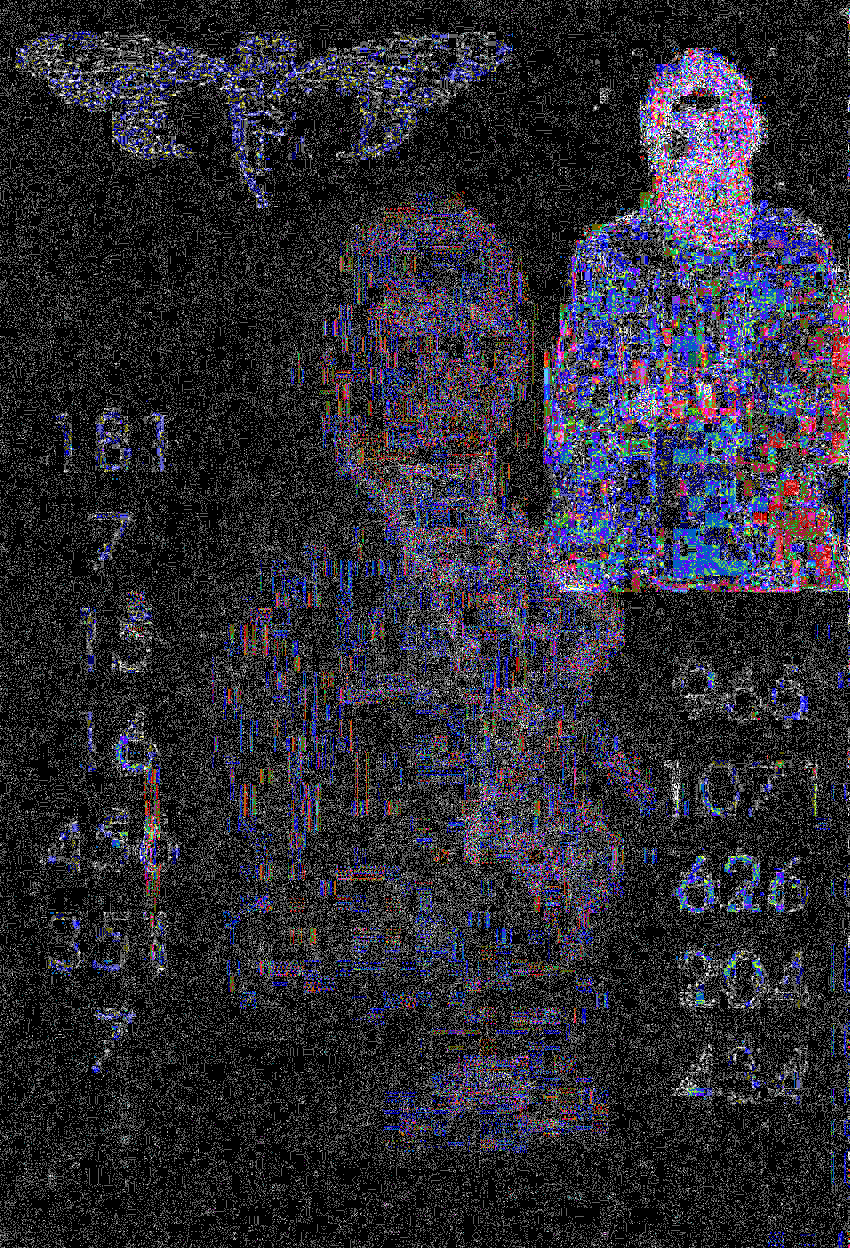
This resulted in a left column of 181, 7, 15, 16, 456, 351, 7 and a right column of 966, 1071, 626, 204 and 434. Sadly this does not appear to be a full magic square and no more numbers could be discovered.
However if you sum the left column and right column:
- 181 + 7 + 15 + 16 + 456 + 351 + 7 = 1033
- 966 + 1071 + 626 + 204 + 434 = 3301
We know we already have a 5x5 magic square that sums to 1033. This left column could be a single column (or row) of the 7x7 magic square and likewise the right column sums to 3301 and could represent the 5x5 magic square that sums to 3301. So now I'm under the belief we don't need any magic square - we need these specific magic squares.
So if we look back at all the assets from that puzzle we had:
- An image of Godel's incompleteness theorem
- An eye (M.C Escher)
- A 3 second audio clip of Bach's Trio Sonata
- The photo above
- An mp3 song (Interconnectedness by 3301)
The first 3 assets are so tiny and were already packed in an image, so there is probably not much luck of finding some hidden magic squares within those. We've already ripped apart the photo above, so I believe we are missing something in the audio file.
With this lets try out stego-toolkit and see if we can detect anything, so knowing we have an audio file that leaves the following tools to check:
AudioStego- CLI Tool, October 2017- mp3stego - CLI Tool, August 1998
spectrology- CLI Tool, October 2015- Steghide - CLI Tool, November 2001
stegpy- CLI Tool, August 2018- SonicVisualiser - UI Tool, May 2007
- OpenPuff - UI Tool, April 2011
DeepSound- UI Tool, October 2023
With the initial release date included I tossed out any tool that was built after the 3rd Puzzle was released (January 2014). It wouldn't make sense to use a stenography tool that didn't exist at time of Cicada puzzles. I'll attempt to use the latest version and version that existed at January 2014 time for each remaining tool.
So with 4 tools left - there was nothing left to do but hammer some testing in hopes to find some hidden answers. Very quickly I learned that most of these tools require a password to decode any possible information within. With no idea what our password could be I started with our existing word-lists that have been collected from the puzzles thus far. Knowing Cicada though - if a password is in-use its probably in front of our face somehow. I'm guessing since we had hints of the squares in the portrait image - it probably has something to do with those numbers.
With the remaining 4 tools lets look at the latest version compared to the version that existed in late 2013 or early 2014.
| Tool | 2014 Release | Current Release |
|---|---|---|
| mp3stego | 1.1.18 (June 13, 2006) | 1.1.19 (November 3, 2018) |
| Steghide | 0.5.1 (October 15, 2003) | 0.5.1 (October 15, 2003) |
| SonicVisualizer | 2.3.0 (December 12, 2013) | 5.0.1 (October 1, 2024) |
| OpenPuff | 4.0.0 (July 10, 2012) | 4.0.1 (July 19, 2018) |
With two tools that are executed via command - we can wire up a quick script to iterate our word-lists, attempt an extraction from each word and alert if a match was found. Of course before doing that, I want to make sure this actually works with the script I've designed. So for each line item I'm going to test encrypt something so I can be positive my extraction is working.
Using stego-toolkit it commonly encrypts using password "abcd" for a demo. So feeding my script an example mp3 encrypted with "abcd" and stored with a hidden message led to a successful extraction.
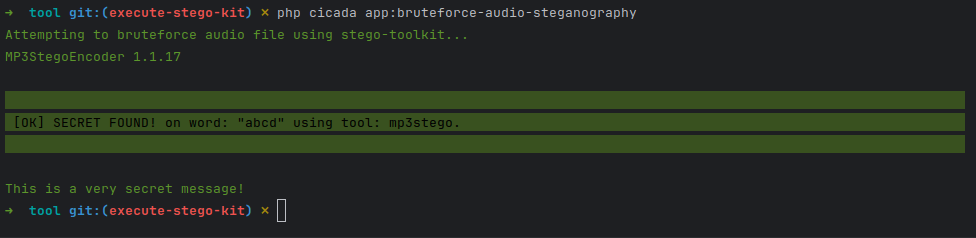
So with that test case completed - I immediately fed it my collected words and this time gave it the Interconnected song. This execution took quite a while (1 hour and 11 minutes) iterating every single word from our custom word lists, but ultimately failed with no discovered messages. I was going to try again on an older version of mp3stego, but all the versions report as 1.1.17 so its a bit difficult to know if I'm using the right old/new version.
So onward to Steghide I went repeating this same exercise, which was immediately way easier due to already having a previously built infrastructure to handle the automation.
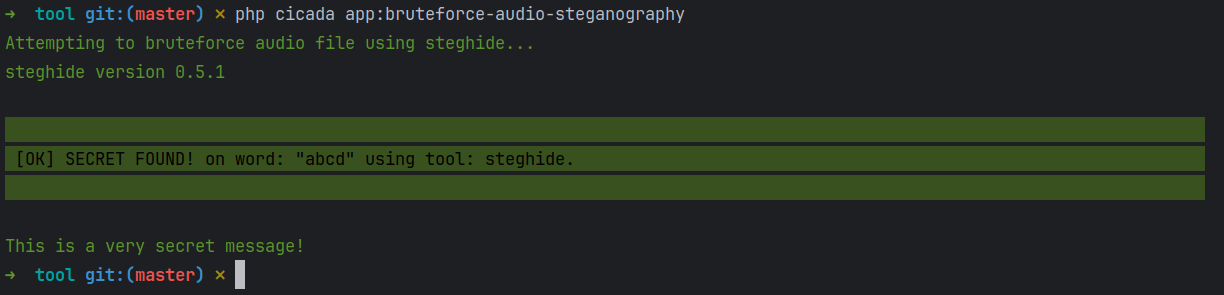
In a quick test I had it working with a sample file to prove extraction of a secret. However when I fed it the Interconnected song it failed to find a match. Thankfully steghide only had one version (0.5.1) between past and now so it was time to move onto SonicVisualiser.
Sonic Visualiser was an interface based tool, so I had to quickly spawn a VNC session which Dominic Breuker made incredibly easy with the stego-toolkit project. However, the downside meant I no longer had a powerful automation script system to leverage.
I loaded up the song into Sonic Visualiser and was personally lost beyond belief. My knowledge using wave-forms, spectrograms and melodic/frequency graphing was next to zero so I had to spend some time learning techniques for discovering information hidden within a song.
With a bit more research I went through the following:
- Spectrogram Analysis - I was looking for some message/code hidden within the spectrogram.
- Waveform Analysis - I was looking for anomalies in the waveform that might suggest some data within.
Success thrives in the world of Sonic Visualiser when you have an original audio file and one you think is modified to compare against. This song produced by Cicada as far as I can tell is an original creation so we have nothing to compare against.
The more I research the audio via Sonic the more I realize Cicada 3301 would not have made something so easy to spot in a tool. Cicada puzzles are resistant to brute-forcing generally so my guess if anything is packed in this file we haven't found it. This tool (Sonic) has gone through nearly 20 versions since 2013, but I'm under the belief tools visualizing data have only improved so I'll ignore the older versions and just move on.
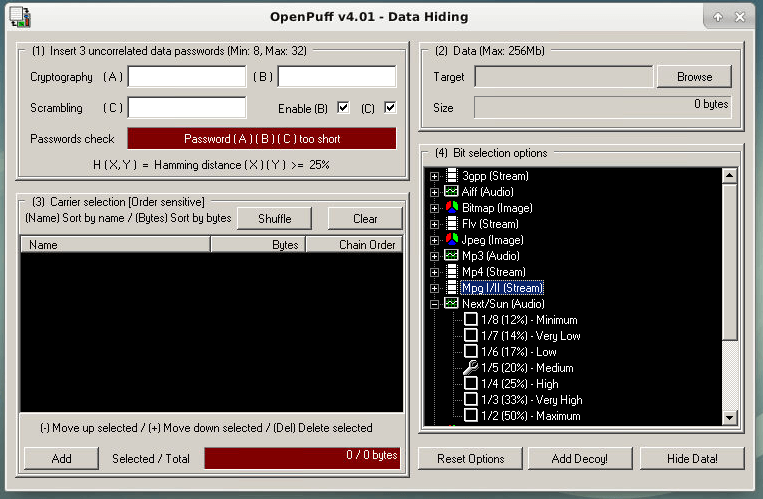
With only one tool left I opened up OpenPuff which is another interface-only based tool. Like our other tools I need to pack a secret to learn how this works. Quickly I learned this is a complex tool with many different possible passwords (A, B and C) and each password has a minimum of 8 characters.
In addition to 3 different passwords (Only A is required) I also need to specify a bit selection option between (12%, 14%, 17%, 20%, 25%, 33%, 50%) so I have my work cut out for me in order to brute-force some guesses.
I first wrote an extension to my Cicada tool to spit out relevant Cicada 3301 words greater or equal to 8 characters.
php cicada app:wordlists 8
certainty
circumference
circumferences
contained
contraries
discerned
discover
distinct
divinity
energies
eternity
existing
experience
following
illusions
innocence
knowledge
necessary
principles
struggle
suffering
tunneling
ultimately
So every morning before work I started a little boring process where I picked a bit percent and went down the list above of words to see if anything would be discovered. This was a painful process that ended every single morning with an error like this.
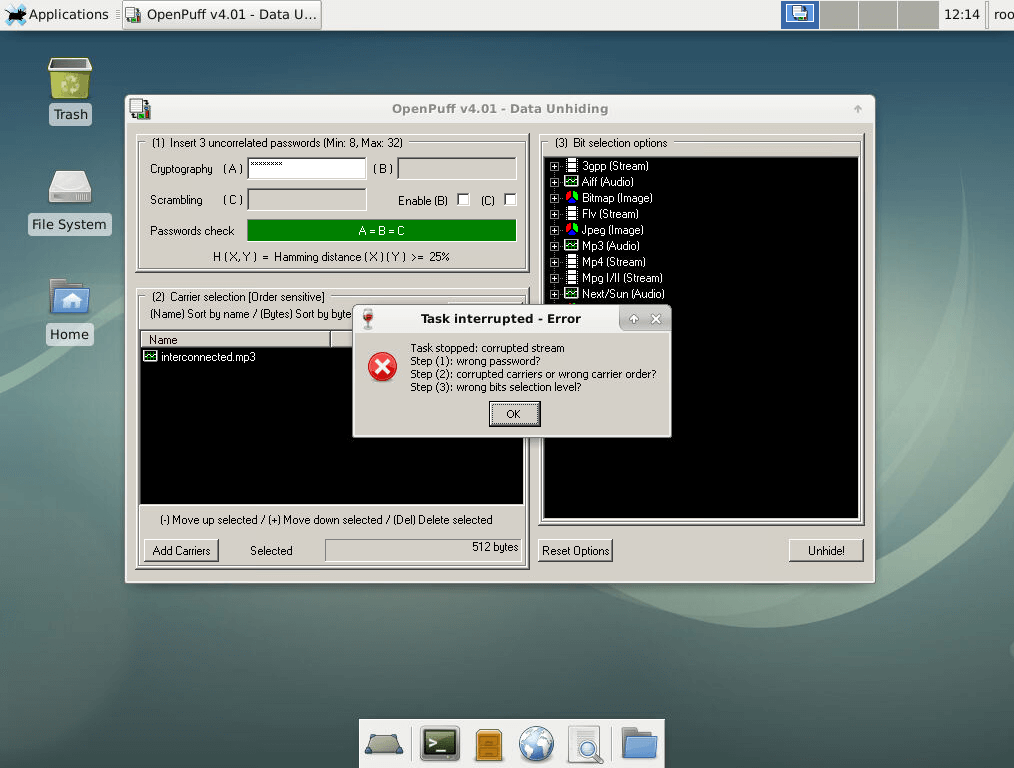
After about a month of daily attempts I decided to put the project on hold once I exhausted all my passwords/percent pairs to attempt. I had tried every single tool with a wide variety of passwords and came up empty. I still had older version of tools to use, but I couldn't muster up the energy to painfully go through all those passwords again.
A few months later I picked this up again and started fresh on retracing all my steps. One thing that caught my eye was the numbers of both sides of the photo that accompanied the audio file. When you summed those you got 1033 or 3301.
181 + 7 + 15 + 16 + 456 + 351 + 7 = 1033
966 + 1071 + 626 + 204 + 434 = 3301
After spending so long with OpenPuff and realizing the minimum password count was 8 - I saw I could combine 1033 & 3301 into an 8 letter password. So I built an iteration for every single combination of 1033 and 3301 and made a new word-list. It was very easy to test, but unfortunately had no luck with any of the previous tools.
I did a bit of research on the state of stenography in 2014 and research kept going back to Embedded SW which was a company that specialized in stenography and security in the early years and growth of online puzzle hunts. I started thinking that most of the tools above were created around the time the 3rd puzzle was released. The author(s) of the Cicada puzzles probably grew up with an older piece of software like anything produced by Embedded SW which started way back in 2004.
So I decided to try again with an older version of OpenPuff (v4.0) and run through my possible passwords again. To my surprise when I hit 33011033 with a 50% bit selection I saw a different message than ever before. I couldn't believe the password was in front of my face the entire time.
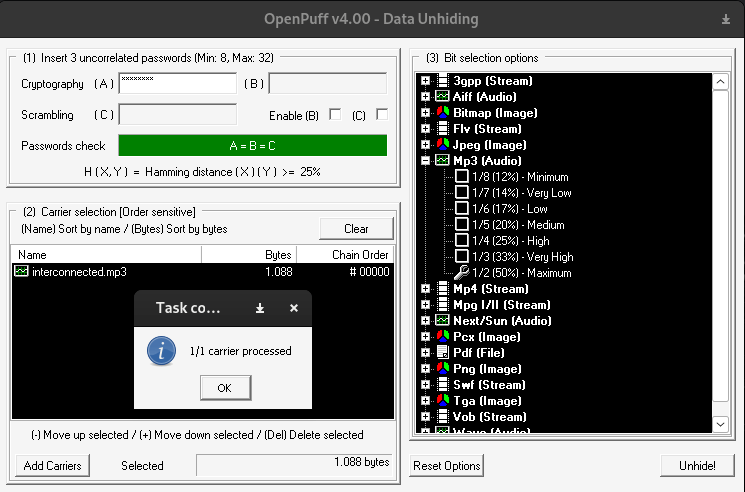
As I hit "Ok" another dialogue popped up with details on what it discovered.
*** Begin of Report ***
Hidden file:
Name <- magicsquares.txt
Size <- 745 byte(s)
CRC32 <- 0x6A8C41E3
*** End of Report ***output from OpenPuff
Success was finally here - a hidden file called "magicsquares.txt" was hidden within interconnected.mp3. This file contained 3 magic squares.
434 1311 312 278 966
204 812 934 280 1071
626 620 809 620 626
1071 280 934 812 204
966 278 312 1311 434
7 375 236 190 27 17 181
351 223 14 47 293 98 7
456 232 121 114 72 23 15
16 65 270 331 270 65 16
15 23 72 114 121 232 456
7 98 293 47 14 223 351
181 17 27 190 236 375 7
272 138 341 131 151
366 199 130 320 18
226 245 91 245 226
18 320 130 199 366
151 131 341 138 272
Immediately I recognized the 3rd magic square as it matched exactly to what was discovered in a previous part of the puzzle. Not only that, but the hidden numbers we found in the image corresponded to the puzzles above.
- 181, 7, 15, 16, 456, 351 and 7 was the last column in the 2nd magic square.
- 966, 1071, 626, 204 and 434 was the first column reversed in the 1st magic square.
So now that we had the magic squares discovered we had to build a TOR website that Cicada would presumably communicate with us through.
We have to host & build a Tor website that supports file uploads (under namefile) at the location of/cgi-bin/upload.
Additionally serving our respective public key at/key.asc
It didn't take long to build a pretty dumb PHP script that would capture files (and other inputs) while hosting my public key. With one simple default nginx change all I had to do was configure a server for TOR hosting. Which wasn't hard at all - just had to tell tor where to access my web server (nginx) and once I had that working I locked down my nginx to only listen on a socket and no longer port 80. This script was going to log nearly everything sent to it in preparation for a possible Cicada contact.
if (!empty($_GET)) {
file_put_contents($logFile, 'GET: ' . print_r($_GET, true) . PHP_EOL, FILE_APPEND);
}
if (!empty($_POST)) {
file_put_contents($logFile, 'POST: ' . print_r($_POST, true) . PHP_EOL, FILE_APPEND);
}
if (!empty($_FILES)) {
foreach ($_FILES as $file) {
$fileLocation = $fileLocation . '/' . $file['name'];
move_uploaded_file($file['tmp_name'], $fileLocation);
file_put_contents($logFile, 'FILE: ' . $fileLocation . PHP_EOL, FILE_APPEND);
}
}Carefully the magic squares were pasted into their respective box, the URL to the created onion was added and "submit" was clicked. Instead of the generic unsuccessful page - we were presented with a simple response page with 3 more book pages!
<html><head></head><body>
<p> Thank you for you submission. </p>
<img src="/107.jpg" /><br />
<img src="/167.jpg" /><br />
<img src="/229.jpg" /><br />


So I had to quickly run outguess over these new book pages, but came up empty with no messages packed within.
It was time to get to work to decode these pages, but first I had to laugh as the magic square I spent months on to find was now just given to us on the 3rd page. After the slow painful process of converting these book pages to runic characters I had a single string that represented each page.
ᚪ ᛋᚹᚪᛁ ᛈᚢᛟᚫ ᛈ ᚠᛖᚱᛋᛈᛈ ᚦᛗ ᚾᚪᚱᛚᚹᛈ ᛖᚩᛈᚢᛠᛁᛁᚻᛞ ᛚᛟ ᛠ ᛄᛖ ᛠ ᛁᚫ ᚷᛖ ᚦᛟᛁᛞᛟ ᛝᚠ ᛄᛖ ᛞᛁᛉᚾᚢᛚᚠᚻᚱᚹᛈᛞᛡ ᚻᚹ ᛋᚳᛉᛞ ᚻᛡᛖᛡ ᛠᚱᛉᛖᛇ ᛒᚹ ᛠ ᛋᛒᛚᛞᚹᛈᚳ ᚫᚩ ᚹᛉᛞᚪᚪᛄᛠ ᚹᚣᛠᚳ ᛄᚪᚳ ᛗᚾᛈᛏ ᚩᚻ ᛗᛈᛗᚳᛡᚱ ᚱᚪᛚᛡ ᛁᛒ ᚠᛋ ᛈ ᚳᛝᛗᚳᚹ ᛁᛗᛗᛁᚪᚻ ᚣᛝᚳᛟ ᛒᛠᛇ ᛁ ᚱᚹᚾᛒ ᛡᚪᛗᛟ ᛈ ᛁᚩᛠᚳᛠ ᛉᚾ ᛚᛏ ᚻᛒᛡ ᛚᛇᚢᚪᚻᚣ ᚷᛖ ᛏᚷᚢᛇᛟᛡᚫ ᚪᛡᛞ ᛖᛟ ᚱᚫᚠᛋᚹᛡ ᚣᛗᛋ ᚣᚪᛗᛡ ᛏᚱ ᚷᛖᚾᚪ ᛚᛡ ᛗᛈᛋᚣᛟᚱ ᚩᚻ ᛗᛈᛗᚳᛡᚱ ᚱᛏᛈᛒ
ᛈᛗᛈ ᚦᚹ ᛗᚳᛁᛞᚹᚾᚣ ᛠᚾᚪ ᚳᚪᛠᛡ ᛚᛡ ᚢᛝᛁᛋᛟ ᚦᚫᚷ ᛄᛗᛗᚳ ᚪᚪᛠᛞ ᚹᚹᚢ ᚾᛉᚢᚹ ᛈᛝ ᛁᚩᛠᚳᛠ ᛉᚾ ᛡᛟᚢᛟ ᛇᛒᚩ ᛁᚱ ᚦᛠ ᛉ ᚪᛁᛈ ᚦᚹ ᛗᚳᛁᛞᚹᚾᚣᛗ ᚹᛗᛞᛖ ᚹᛈᚾᛗᚷᚣᛏᛠᛈᛖᚪ
ᚪᚾ ᛁᚾᛋᛏᚱᚢᚳᛏᛡᚾ ᚳᚹᛖᛋᛏᛡᚾ ᚪᛚᛚ ᚦᛝᛋ ᛞᛁᛋᚳᚩᚢᛖᚱ ᛏᚱᚢᚦ ᛁᚾᛋᛁᛞᛖ ᚣᚩᚢᚱᛋᛖᛚᚠ ᚠᚩᛚᛚᚩᚹ ᚣᚩᚢᚱ ᛏᚱᚢᚦ ᛁᛗᛈᚩᛋᛖ ᚾᚩᚦᛝ ᚩᚾ ᚩᚦᛖᚱᛋ ᚳᚾᚩᚹ ᚦᛁᛋ 434 1311 312 278 966 204 812 934 280 1071 626 620 809 620 626 1071 280 934 812 204 966 278 312 1311 434I ran each string through a basic translate/reverse and surprisingly the last page decoded successfully.
AN IN[S|Z]TRU[C|K]T[IA|IO]N [C|K]WE[S|Z]T[IA|IO]N ALL TH[NG|ING][S|Z] DI[S|Z][C|K]OUER TRUTH IN[S|Z]IDE YOUR[S|Z]ELF FOLLOW YOUR TRUTH IMPO[S|Z]E NOTH[NG|ING] ON OTHER[S|Z] [C|K]NOW THI[S|Z]
434 1311 312 278 966
204 812 934 280 1071
626 620 809 620 626
1071 280 934 812 204
966 278 312 1311 434
The oddity occurs with what is clearly "Question All Things". You can see the only options we have is C or K, when we expected Q.
[C|K]WE[S|Z]T[IA|IO]N ALL TH[NG|ING][S|Z]However, we know from the Gematria Primus that we don't have the letter Q as a possibility. So the last page (Page 16) breaks down to:
AN INSTRUCTION
KWESTION ALL THINGS
DISCOUER TRUTH INSIDE YOURSELF
FOLLOW YOUR TRUTH
IMPOSE NOTHING ON OTHERS
KNOW THIS
434 1311 312 278 966
204 812 934 280 1071
626 620 809 620 626
1071 280 934 812 204
966 278 312 1311 434Now I was back to the other 2 pages that didn't seem to decode in that same manner. So I began running some brute-force little scripts I wrote. I took the first few characters (ᚪ ᛋᚹᚪᛁ ᛈᚢᛟᚫ ᛈ) of the 1st page and used it to test some column shifts, rotation shifts and vigenere shifts.
As I was scrolling the output on the vigenere shift I saw something interesting.
| Word | Translation |
| circumference | M [C|K]OMN DUR[NG|ING] A |
This appeared to spell the word "During" with a vigenere key of "circumference", but it didn't look perfect. In one of the earlier parts (Part 3) of this puzzle we spent a lot of time on decoding a koan. As I look at this failed decoding - the phrase looks pretty close to "A Koan - During a"
So now we have a problem - I'm fairly sure the key is circumference, but not spelled exactly that way. So if we take the original runic to human letter conversion we get this:
A [S|Z]WAI PUOEAE PWhich suggests the first character is already correct. However, by the time we move down the key (circumference) we fix the word of PUOEAE to DURING. So this suggests if we examine the key in detail the 1st character (c) is affecting the shift, but the 2nd and 3rd seems fine. We also know the 4th character (c) is also breaking the decoding, so I believe we have a pattern.
I believe the leading c's in circumference (or maybe all) need to be changed. This is classic behavior of Cicada puzzles to thwart basic automation. So there are 2 paths to take with this - we can assume a single character (a|ᚪ) shouldn't be shifted or we record the runic indexes to skip.
Neither of these options worked.
- If you ignore a specific letter - decoding falls apart into unreadable text.
- If you skip specific indexes you break the string as it shifts the key into phrases that we previously correct.
We basically need to change the key to something that won't break our parser and there is one special character in the Gemetria Primus. The first character (0 index) in the translation guide is the letter f. So if we adapt our vigenere key to "firfumference" we may have better luck as that letter in a key will cause the character to not shift any direction.
➜ php cicada app:vigenere
Enter a sentence to translate:
> ᚪ ᛋᚹᚪᛁ ᛈᚢᛟᚫ ᛈ
Enter the key.:
> firfumference
Enter the indexes to skip.:
>
Translation: A [C|K]OAN DUR[NG|ING] A
https://github.com/iBotPeaches/cicada_3301/blob/master/tool/app/Commands/TranslateVigenere.php
This seemed to work but I was only decoding 15~ characters so time would tell if that was the full string. To help understand how this worked it may help to first visualize how this algorithm was working for the original key of "circumference".
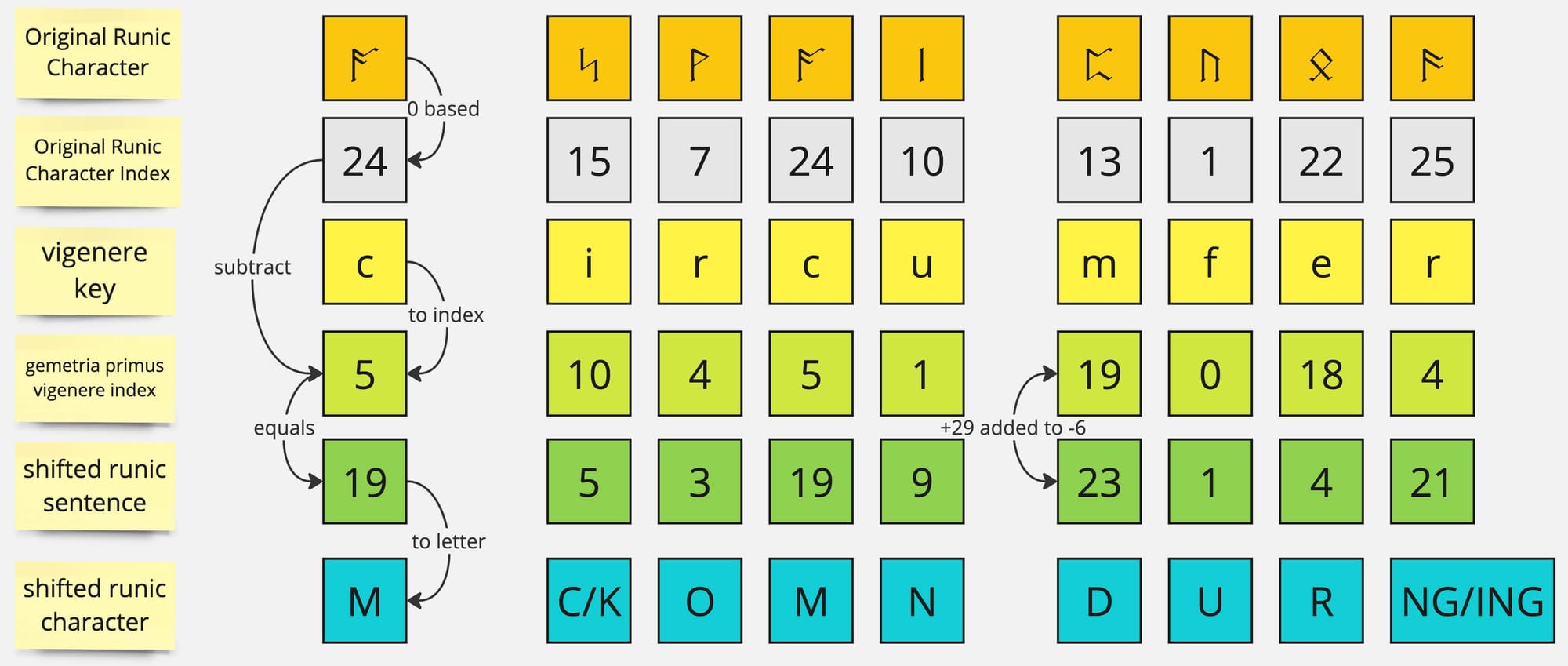
As you can see above - we take the original runic character and identify its index starting at 0. We take our key and convert/translate it to runes in order to find its index (also 0 based) in the Gematria Primus. Once we have a numeric for both the string and key - we do a simple subtraction. If we happen to go into the negatives we add the amount of runes (29) to the value to wrap it back into positive values. This gives you the shifted numbers which can be easily translated into letters.
Now visually you can see that the letter F above represents 0 which means the value did not shift from its original numeric index. So we can remake the image above with the corrected key to see the impact.
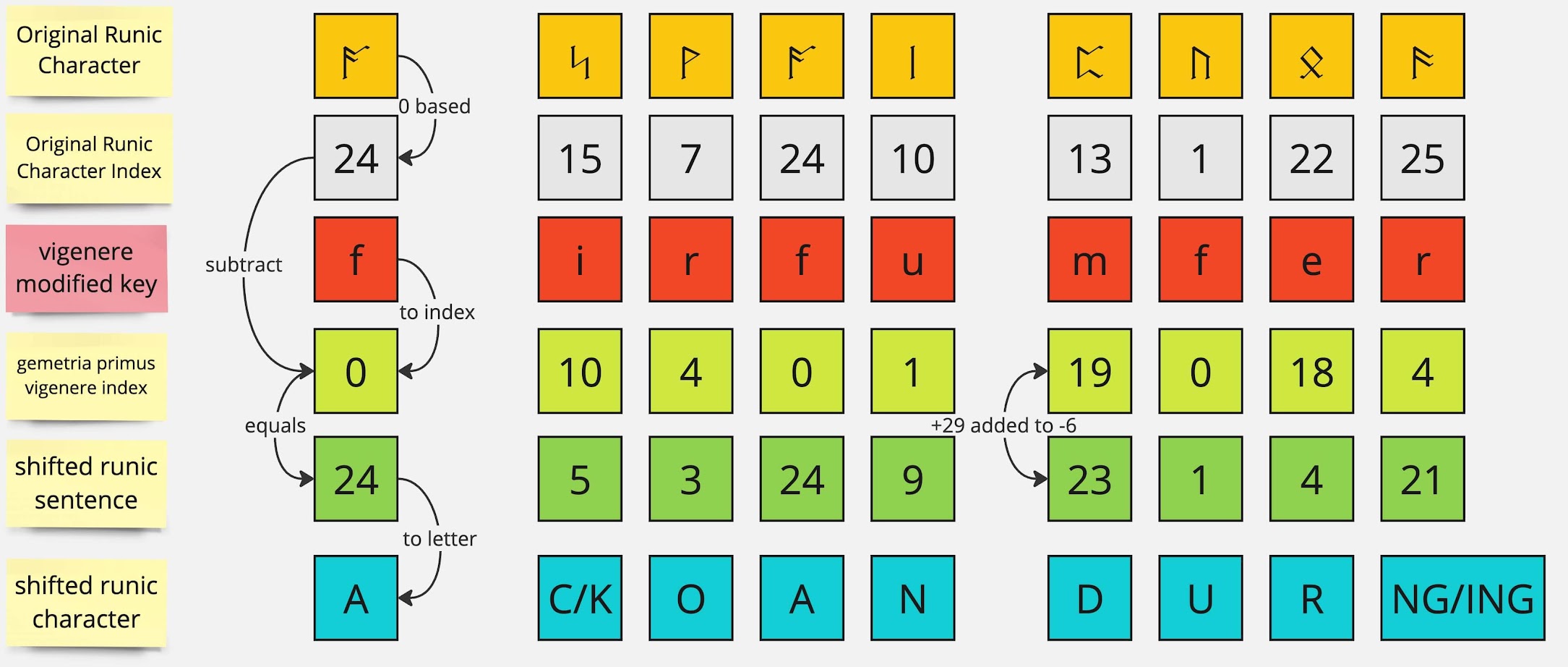
Now you can see how the string decodes correctly without affecting the other characters. So I grabbed the entire single line runic string and attempted a decoding and it quickly fell apart after "During". However, I saw another letter "c" towards the end of the word circumference, so I tried using firfumferenfe where I changed all letter C's to F's.
This had more success, but then fell apart a bit into the sentence.
Translation: A [C|K]OAN DUR[NG|ING] A LE[S|Z][S|Z]ON THE MA[S|Z]TER EXPLAINED THE I THE I I[S|Z] THE UOI[C|K]E OL JF DFINFUFMFERDNThankfully a few onions ago we had developed indexes to skip as an optional extension to the vigenere cipher, so I carefully started recording indexes where the decoded string fell apart. It only took two indexes (65, 76) skipped and the entire page decoded into something readable.
A [C|K]OAN
DUR[NG|ING] A LE[S|Z][S|Z]ON
THE MA[S|Z]TER EXPLAINED THE I
THE I I[S|Z] THE UOI[C|K]E OF THE [C|K]IR[C|K]UMFEREN[C|K]E HE [S|Z]AID
WHEN A[S|Z][C|K]ED BY A [S|Z]TUDENT TO EXPLAIN WHAT THAT MEANT
THE MA[S|Z]TER [S|Z]AID IT I[S|Z] A UOI[C|K]E IN[S|Z]IDE YOUR HEAD
I DONT HAUE A UOI[C|K]E IN MY HEAD THOUGHT THE [S|Z]TUDENT
AND HE RAI[S|Z]ED HI[S|Z] HAND TO TELL THE MA[S|Z]TER THE MA[S|Z]TER [S|Z]TOP...So I quickly had to check if the next page (Page 15) stood on its own or had to be decoded with the same key alongside the previous page. The next page had to be decoded after it was added to the end of the previous page. This added the following snippet.
[S|Z]TOPPED THE [S|Z]TUDENT AND [S|Z]AID THE UOI[C|K]E THAT JU[S|Z]T [S|Z]AID YOU HAUE NO UOI[C|K]E IN YOUR HEAD I[S|Z] THE I AND THE [S|Z]TUDENT[S|Z] WERE ENLIGHTENED
So with a bit of cleanup. I could clean up the entire 3 pages into a one solid story.
A Koan
During a lesson the master explained the I:
"The I is the voice of the circumference" he said.
When asked by a student to explain what that meant,
the master said, "It is a voice inside your head."
"I don't have a voice in my head," thought the student
and he raised his hand to tell the master.
The master stopped the student and said: "The voice
that just said you have no voice in your head is the I."
and the students were enlightened.
An Instruction
Question all things
Discover truth inside yourself
Follow your truth
Impose nothing on others
Know this:
434 1311 312 278 966
204 812 934 280 1071
626 620 809 620 626
1071 280 934 812 204
966 278 312 1311 434
It seemed we successfully understood these 3 pages - now we were just waiting for Cicada to utilize our onion service we uploaded. For some in early May 2014 (and others a bit earlier) Cicada triggered 3 web requests to your onion server.
GET /key.ascwithCicada/33.01 CicaDOS 1.033 E EditionUser Agent.GET /withCicada/33.01 CicaDOS 1.033 E EditionUser Agent.POST /cgi-bin/uploadwithCicada/33.01 CicaDOS 1.033 S EditionUser Agent.
Cicada obtained your public key to be able to encrypt communication solely to you and then confirmed your onion was accessible before uploading a signed message to your host. For some their journey was over and instead a welcome questionnaire message was uploaded which awaited their results. For the majority of folks - the puzzle was not yet over as they received a message to another onion.
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
Hello. Your enlightenment awaits you.
ky2khlqdf7qdznac.onion
We look forward to hearing from you.
Good luck.
3301
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v1.4.11 (GNU/Linux)
iQIcBAEBAgAGBQJTO88vAAoJEBgfAeV6NQkPEfsQAI0jGcmBaQr2AGGr1/ic839I
fc58EyVNLgWs6Aox0/Dc2Tj8dXOxc0sBNWY98tICIy2T0Vbpf1VF65nFs+cVcxXI
pXIU5X0O3XKRfxequIZQQUnt4elLIfFAIgrXbE9N7K5qkD47xg4kaYkPQh7/mDBa
NBVHsLkw8bbLUo7lBtv5VFHTeTikSnT3m7FsoSHl5WlsY9WvITO5VcYd48jFbBSS
P9Uk7v7cg1ohWpDB0BiYUTfOVxXYuZpnFiR6vAADP5KkY/qrFF7wrpYbhSmageId
Qcxyc/dajUTlwK7dl+OwAJn4XRPceBPMjW9SbCr33y1C3ijCuxn06penu0KnUyge
yYjyedXg11UPb/B6eT+hwAOPg/DLDTQ57QOQlGOX19lB56iZbHKuglQZUZ5kJq54
dTobWhi6FBtwu+QLnJCz2SASLCuKDIWFkwSoYro/F9Zlo7b0UUO2IOkcKw7tKzq9
uyPtBDQayCSIIHJhVjAtNiVFjNe+TcBf1VppAGY/7jfUfwxJ7Sfbv5Jwll+6MDYr
YdsnJBZjhLuoxFyr9g4TF0OTXmxT+TyAZ4qoItu4C0bcEncBcfLJz+J74X1upsZl
DMq7On1paQAkXvzr6ywDBpMJbDZETkl9gZbzHn1Ji+9f3fANrqU+5kZ1su2OReQf
++CO13gAUF4WohKip4mC
=VAo/
-----END PGP SIGNATURE-----As folks quickly arrived at a new onion they were left with an alarming sight. Which can best be captured with this little video below.
scrolling "ky2khlqdf7qdznac.onion" at 30% zoom.
It seemed we now had the full book titled Liber Primus in front of us, which was a daunting 75 pages of runic characters. Sure we had probably already decoded 17 of those, but there was nearly 60 remaining. At this point with a huge book and no clear path on the direction to take - things slowed down massively among the public Cicada researchers. We can only assume those really progressing the puzzle succeeded enough to go silent, but surely most folks just worked in private not sharing their success as Cicada recommended.
So Part 4 comes to an end and our next post will be less of a linear journey in parts, but a deep dive into a group/single page of the Liber Primus.
- Puzzle 1 (2012)
- Puzzle 1 - 2nd Chance (2012)
- Puzzle 2 (2013)
- Puzzle 3 - Part 1 (2014)
- Puzzle 3 - Part 2 (2014)
- Puzzle 3 - Part 3 (2014)
- Puzzle 3 - Part 4 (2014) - You are here.
