PiVPN + Pi-hole
Last month I wanted to upgrade my Pi-hole suite of tools in order to gain the benefit of its features while I'm out and about. So I went googling and stumbled upon the official guide for setting up OpenVPN. The thing is though, while looking at those docs I saw an entry on the sidebar for Wireguard.
Wireguard was the biggest news when it got merged for the upcoming Linux Kernel 5.6 release. No longer would you need to build a kernel module to use this extension - it would be available in the Linux kernel itself. This was around the start of the pandemic and I knew it would take a bit of time for systems to react to this new feature, but sure enough Pi-hole community plugins did.

For those unaware, Wireguard is basically a modern VPN tunnel. Gone are the days of modifying 20+ files and configuring something that is decades old. Wireguard is configured pretty much like doing SSH key pairs. You generate a key pair on the Wireguard server and it generates the config needed for your client device.
Depending on the client (phone or desktop) there may be a simple tool to import it, otherwise a simple few commands will get you up and running. I've set up my phone that had an official application which was also open source as well as setting up my hobby laptop.
So now when I grab my laptop and head to a nerd meetup or conference. I'm set with a good encrypted connection back to my house as well as gaining the benefits of my Pi-hole which handles the blocking of anything privacy invasive. A few more dedicated individuals will claim my ISP is evil and I need a real VPN in a different country, but for my use case - this is perfect.
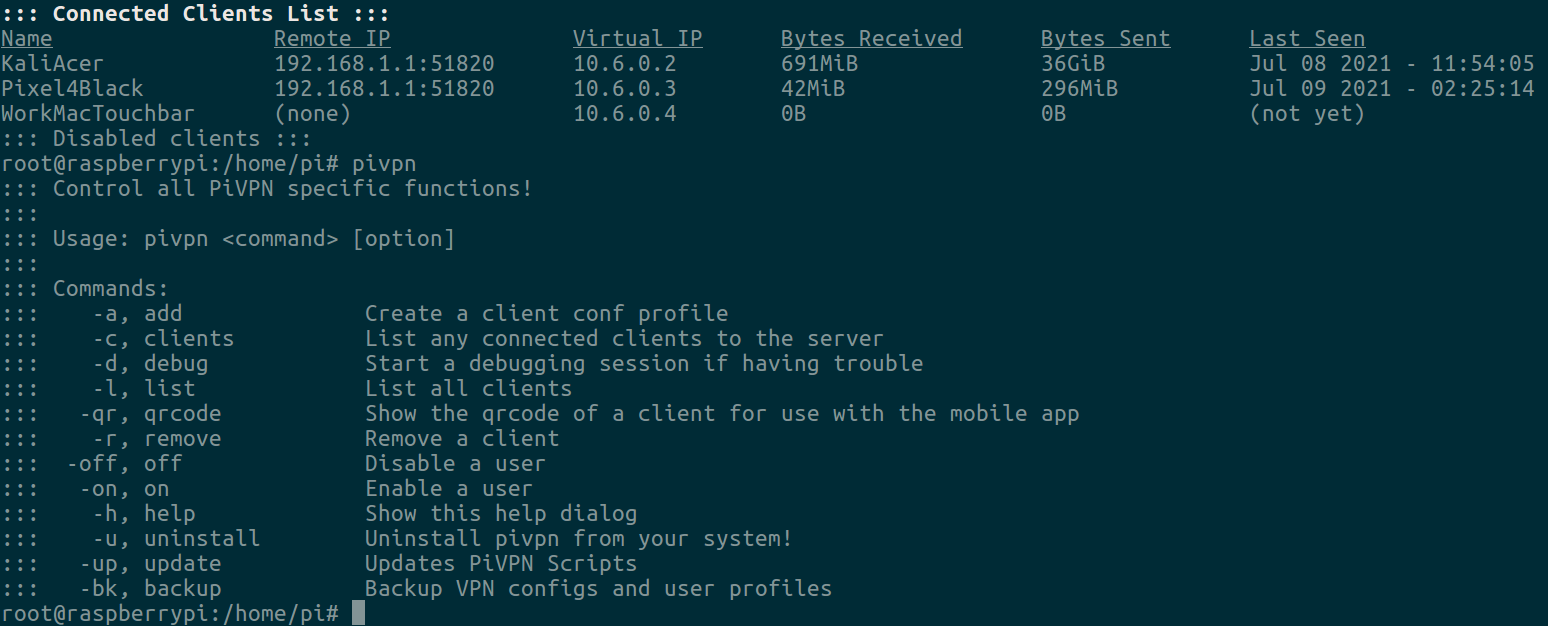
So this entire installation was made easier by a helper script known as PiVPN. The security professionals will say never to install software this way, but don't worry - I reviewed the script and painfully read the large bash script and it looked safe. You may do the same thing before installation if you want.
It automated the configuration of needed tools and setting up proper networking to support a VPN. It additionally built its own structure of config files so I may add one as easy as pivpn add.
root@raspberrypi:/home/pi# pivpn add
Enter a Name for the Client: blogpost
::: Client Keys generated
::: Client config generated
::: Updated server config
::: Updated hosts file for Pi-hole
::: WireGuard reloaded
======================================================================
::: Done! blogpost.conf successfully created!
::: blogpost.conf was copied to /home/pi/configs for easy transfer.
::: Please use this profile only on one device and create additional
::: profiles for other devices. You can also use pivpn -qr
::: to generate a QR Code you can scan with the mobile app.
======================================================================So now I can take that QR code to easily setup a device.

pivpn -qrDon't worry about trying to jump onto my network with that configuration. I have removed that test client, but just wanted to show the ease of use of generating a new one. For those that remember older VPN software - it was not that easy and this wrapper (pivpn) makes it even easier.
For the classic issue of dealing with a semi dynamic IP - I can't place why or when, but a few times a year my IP with Frontier changes. Paying for a static IP is a bit more money and it doesn't take too long to update a DNS record on my server. I should dig into automating that, but it happens rare enough that I can fix with not much effort.
So now I have my own VPN (wireguard.connortumbleson.com) setup running off a Raspberry Pi hanging from a cable in my office. A few tools that when put together which makes a home office and remote home office even better.
