Setting up Nzyme
A couple months ago I was at a talk when I learned about a piece of software that is common in home labs. I listened to a talk by Vodkanaut and he demoed Nzyme and it looked quite interesting, so I spent some time setting up the project as well.
The project in short is a forensic piece of software for WiFi networks. It can log frames and compare to signatures and patterns to provide a constant source of updates of the state of your wireless network. It was built by Lennart Koopmann who was the name behind Graylog2.
The documentation on the project website guides you through the installation and you can follow that without an issue. So I decided to buy a new Raspberry Pi 4 and a Panda Wireless PAU09 N600 - this is one of the devices that is recommended as being able to support monitor mode and working with the project.
One thing I encountered that I highly recommend doing is setting up predictable interface names. As described, this moves things like wlan0 to something consistent for that device like wlp1s0u1u2. This helps so you can ensure you are talking to the right adapter that supports monitor mode vs the inline wireless that is common on most Pi's.
wlan0 IEEE 802.11 ESSID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=31 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management:on
wlp1s0u1u2 IEEE 802.11 Mode:Monitor Frequency:2.484 GHz Tx-Power=20 dBm
Retry short long limit:2 RTS thr:off Fragment thr:off
Power Management:offAs the documentation suggests, you may run into some problems having libpcap automatically configure monitor mode like I did. This means I manually configured my device to keep it in monitor mode, then told nzyme to not worry about it.
802_11_monitors: [
{
# The 802.11/WiFi adapter name. (from `ifconfig` or `ip link`)
device: wlp1s0u1u2
# WiFi interface and 802.11 channels to use. Nzyme will cycle your network adapters through these channels.
# Consider local legal requirements and regulations.
# See also: https://en.wikipedia.org/wiki/List_of_WLAN_channels
channels: [1,2,3,4,5,6,7,8,9,10,11,12,13,14,36,38,40,42,44,46,48,50,52,54,56,58,60,62,64,100,102,104]
# There is no way for nzyme to configure your wifi interface directly. We are using direct operating system commands to
# configure the adapter. Examples for Linux are in the documentation.
channel_hop_command: "sudo /sbin/iwconfig {interface} channel {channel}"
# Channel hop interval in seconds. Leave at default if you don't know what this is.
channel_hop_interval: 1
# Time this monitor can remain without recording any frames until it is marked as failing. Under certain conditions,
# it can be normal to not record any frames for an extended period of time. If you receive warnings and alerts for
# failed probes when there were simply no frames to record, increase this value. Default: 60
max_idle_time_seconds: 60
# Skip the automatic monitor mode configuration of this interface. Only enable this if for some reason libpcap can't
# properly configure this interface into monitor mode. In that case, you can try to set it manually instead.
skip_enable_monitor: true
}
]/etc/nzyme/nzyme.conf
So knowing that the automatic configuration of libpcap wasn't quite working, I leveraged a network config file at the system level and then set skip_enable_monitor above to true.
root@raspberrypi:/home/pi# cat /etc/network/interfaces.d/wlp1s0u1u2
auto wlp1s0u1u2
iface wlp1s0u1u2 inet manual
wireless-mode monitorThese changes paired together got my external adapter in monitor mode, surviving reboots and booting up with nzyme successfully.
So now it was time to setup a nightly email to send me a report of my network.
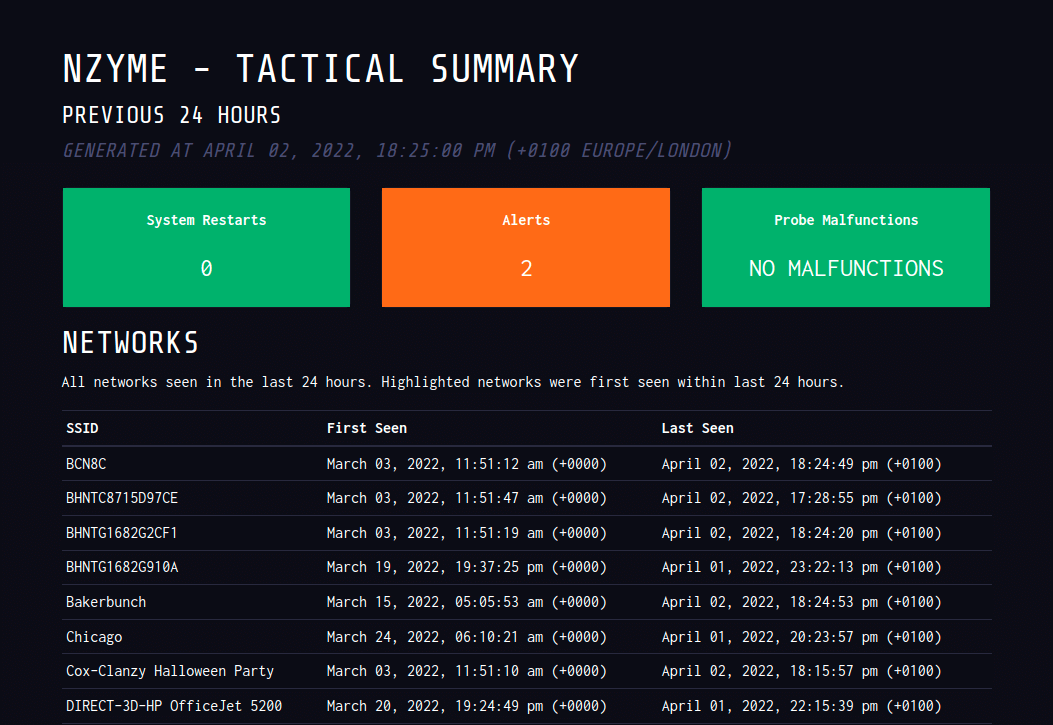
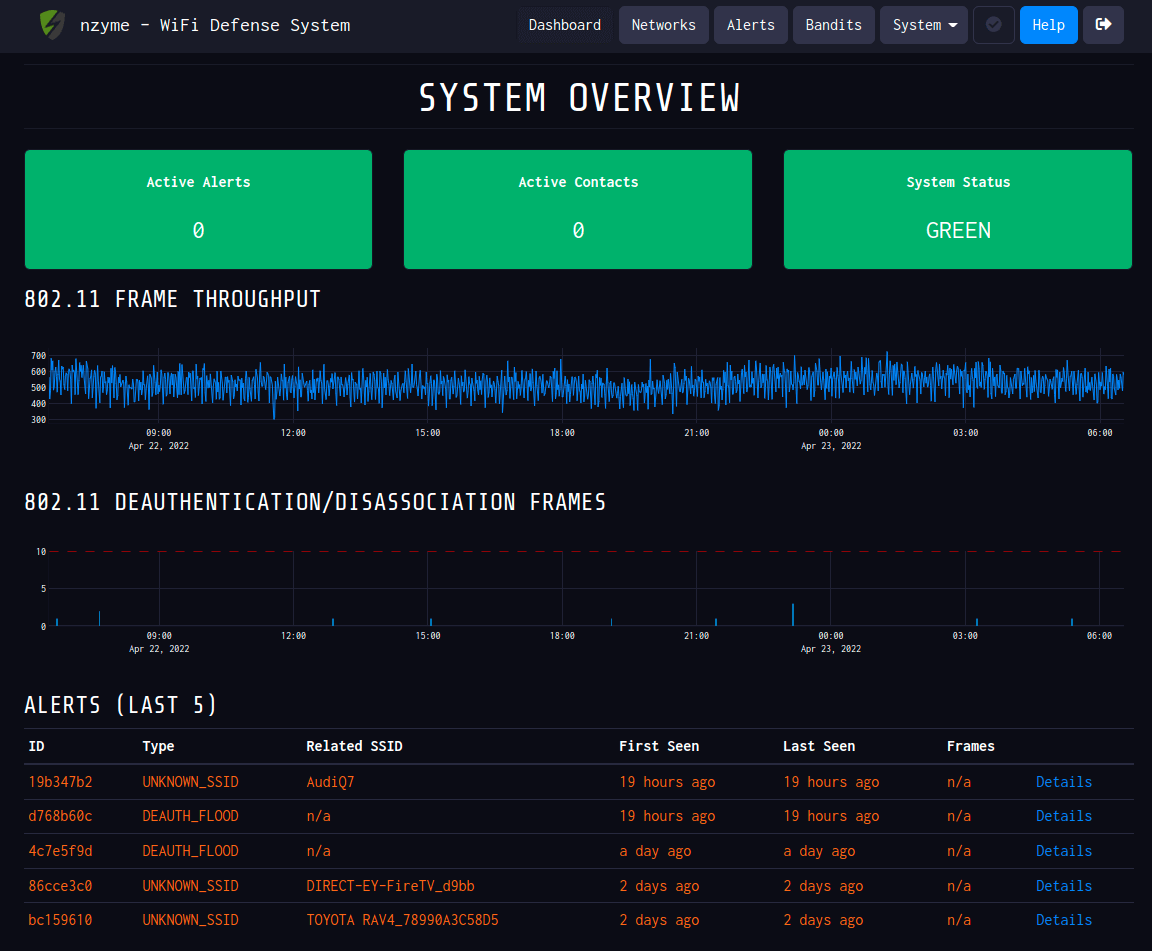
So I get a cool email that shows me:
- Alert count
- Health check
- Status of all networks seen in past 24 hours
- Any new networks
- Any new alert/tracker detected
Now nzyme even shines when you decide to monitor a network, so I monitor my home network (xb0x).
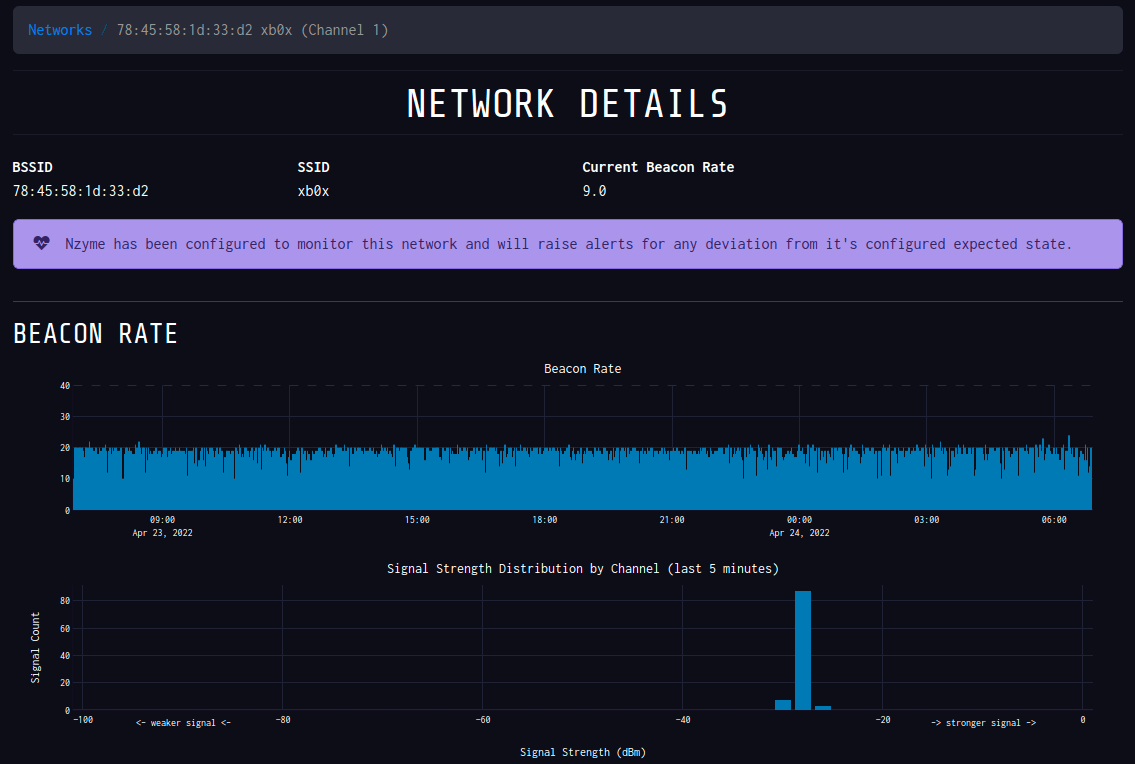
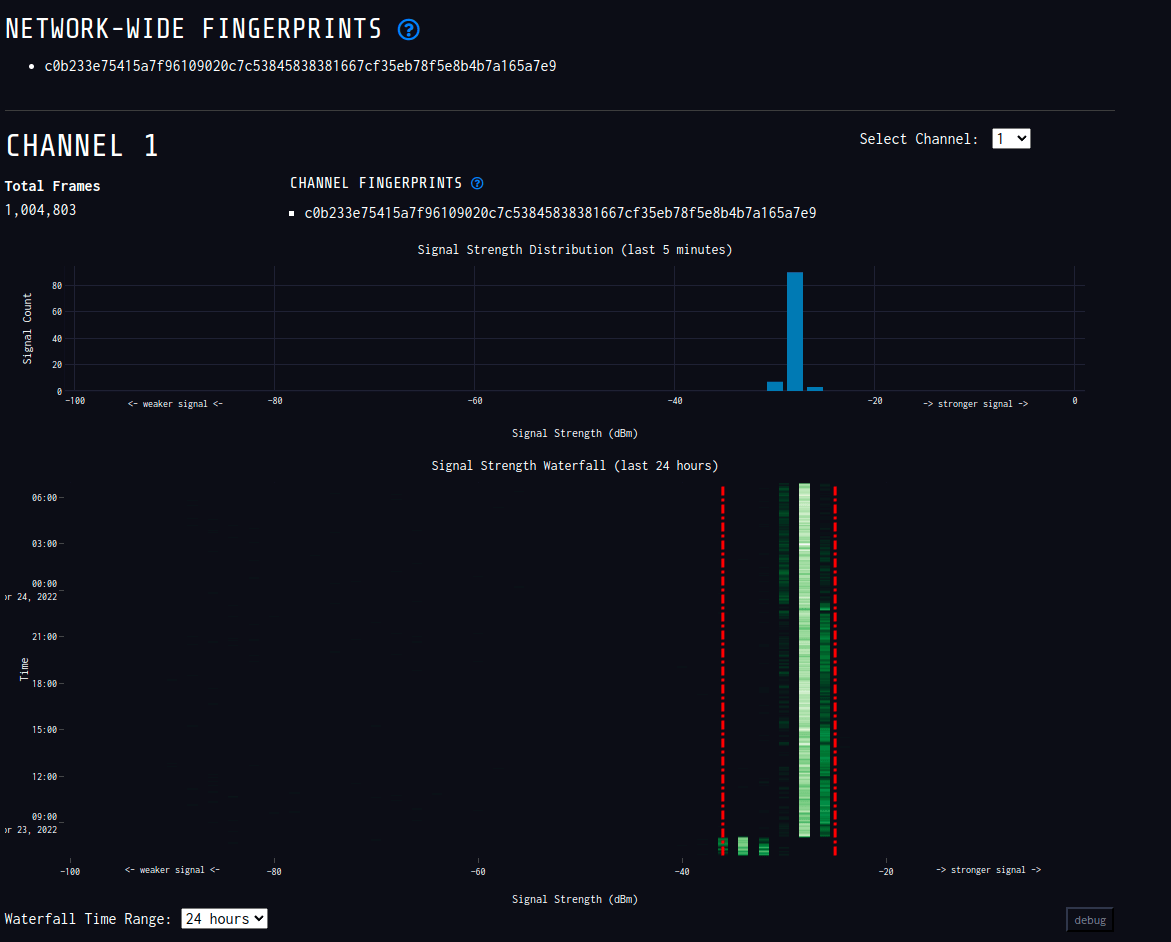
/network/show page in nzyme
This is probably more paranoia than anything, but I can really see into my network to see if anyone else is attempting to deauth me and/or replicate my network with a spoofed one.
On top of specifically monitoring a network - I can globally listen to a growing list of signatures that recognize unique devices. This would basically be devices built by HAK5 or a Pwnagotchi.
So I turned on my Pwnagotchi and waited a few moments until it popped up as an active alert (PWNAGOTCHI_ADVERTISEMENT) in nzyme.
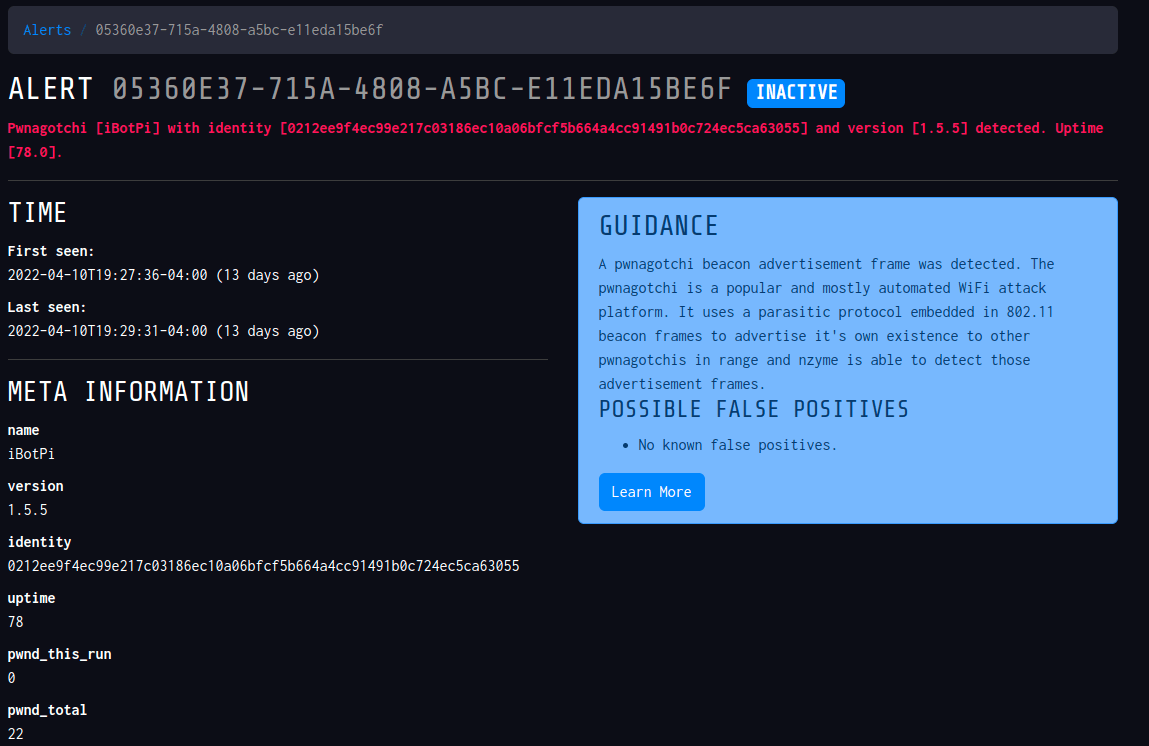
So now I have a cool little peace of mind if anyone is trying some clever network attacks near my home network.
The project is open source and looks to be growing with a new major UI refresh designed as "2.0.0". The current version I'm running is 1.2.2 so I'm excited to see what a refreshed interface looks like.
