OPNsense, WireGuard & Pi-hole
A few months ago I finished a mini home-lab build out to support some new cool technology in my network. After a few more weeks - its all been perfected and I want to walk through supporting a few things:
- A VPN you can use anywhere that supports WireGuard to connect back home.
- Pi-hole to route all traffic over the network or VPN.
- All wired up and configured properly through OPNsense.
Now I started following this official OPNsense tutorial on setting up WireGuard and it worked fairly well, but knowing my setup had a few differences left me to figure it out myself. Now from someone moving from purely ISP consumer based software - this was a bit to learn.
I had some strange issues that like only the first device setup in my WireGuard worked, or when I enabled Wireguard all my non-VPN devices lost Internet. I was quickly learning the true advanced settings for configuring interfaces and routing traffic properly.
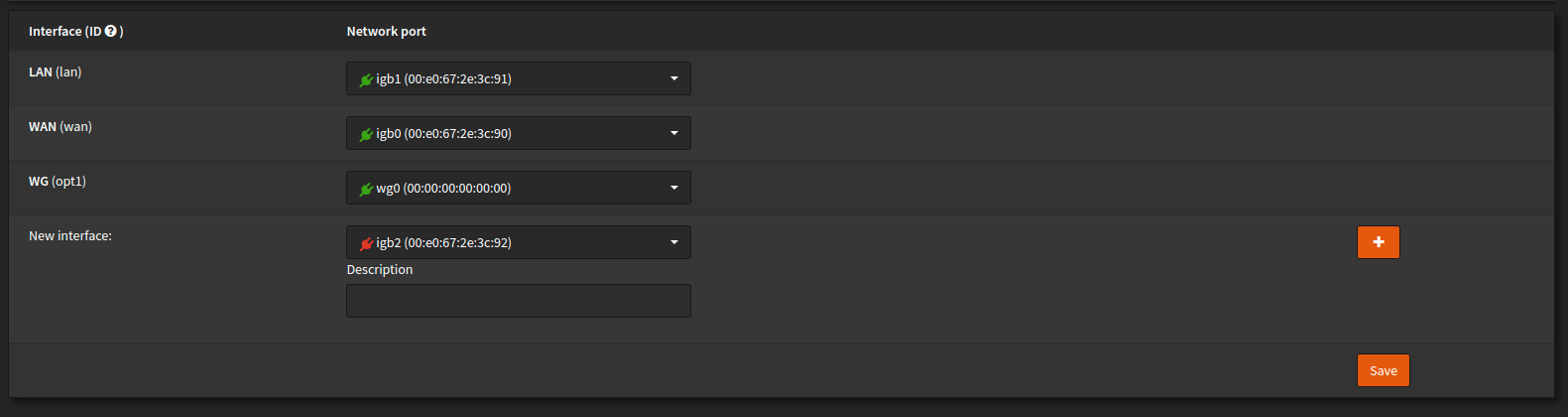
At first I created an interface for WireGuard, this just made things easier for a few reasons:
- Automatic outbound NAT rule creation
- Automatic alias generation for the tunnel
- A good clean separation of rules
So now I just needed to edit that interface to disable the configuration of IPs on it knowing that configuration would occur as Wireguard tunneled to my existing LAN.
Next I needed to open something up on the firewall itself to allow inbound connections to WireGuard server itself.
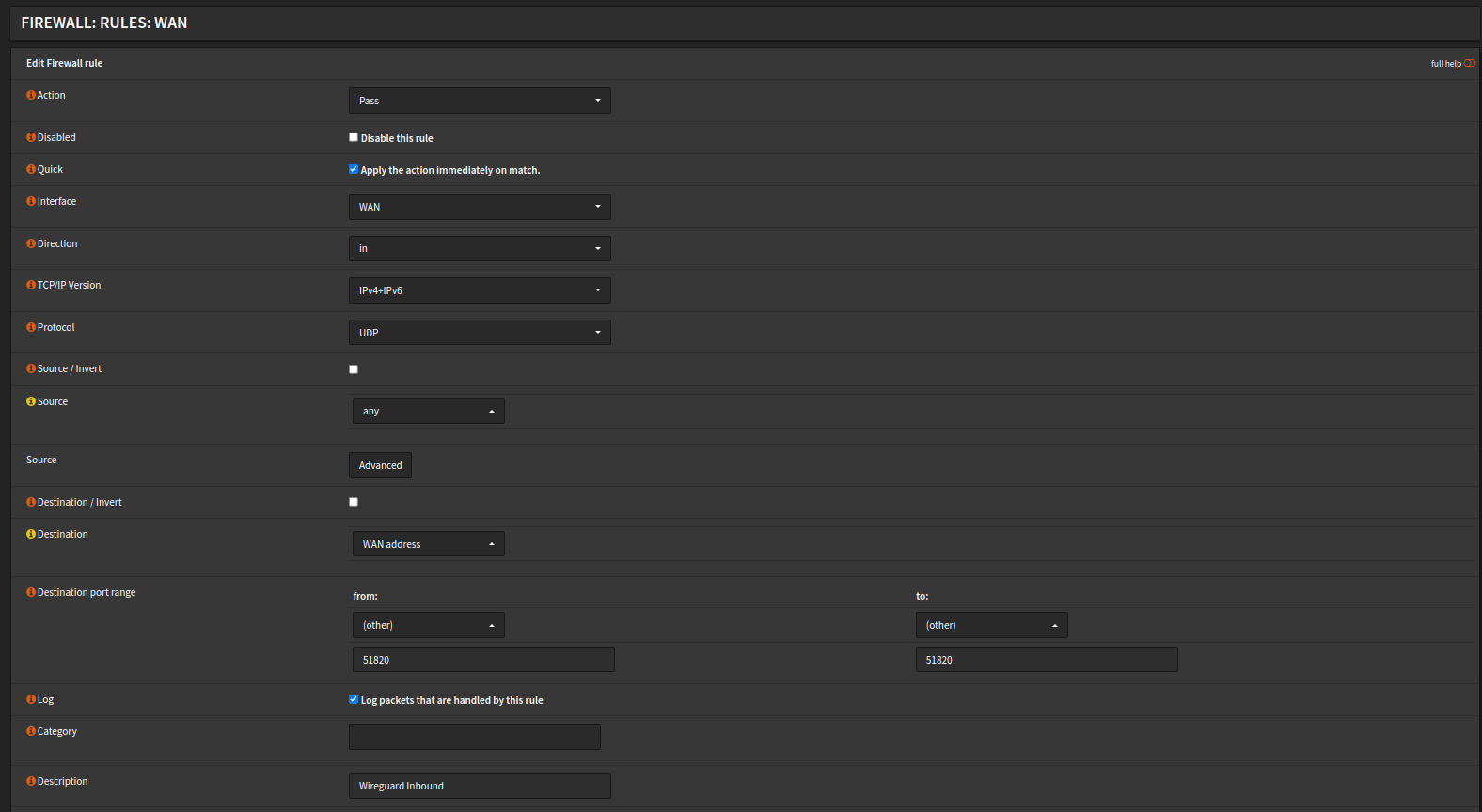
This rule is pretty easy to understand just basically says:
- Inbound connections (IPv4 or IPv6) is allowed under UDP to port 51820
- The source being anything to arrive at the "WAN address"
So now we've basically setup the routing to allow a foreign connection (provided it authorizes) to connect to our WireGuard interface. At this point, we need to create another Firewall rule that determines what can be visited.
For me, I want my VPN remotely to be able to connect to anything local as well as anything on the public Internet. This is so my browsing both at home and afar can benefit from the Pi-hole.
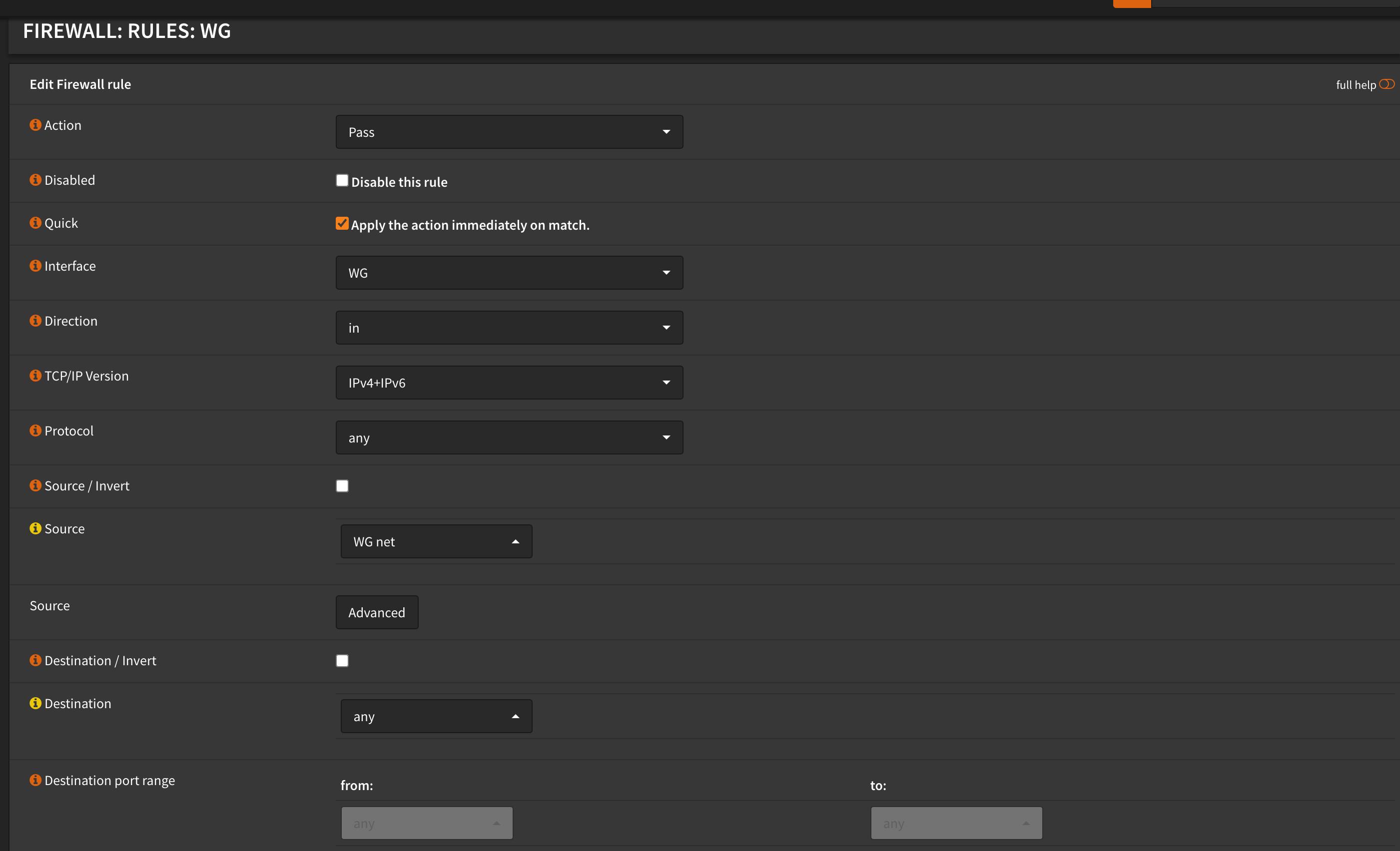
Likewise for this rule - it is pretty easy to follow. We want:
- Any connection into WG (WireGuard) to be allowed anywhere (any)
- For IPv4 or IPv6
So now after these configurations we are ready to setup WireGuard itself. Which you can do from "Services -> VPN -> WireGuard" . This is a powerhouse of configurations allowing multiple VPNs as well as peers. You'll want to make a new connection with the following values:
- Listen Port: 51820 (default)
- Tunnel Address: 10.6.0.1/24 (personal preferred range)
- Disable Routes: true (as it will conflict with our Pi-hole)
The rest you may leave blank as they will be generated automatically. If you are transferring from an existing WireGuard setup - you will want to use those values instead of making new ones so existing clients aren't affected.
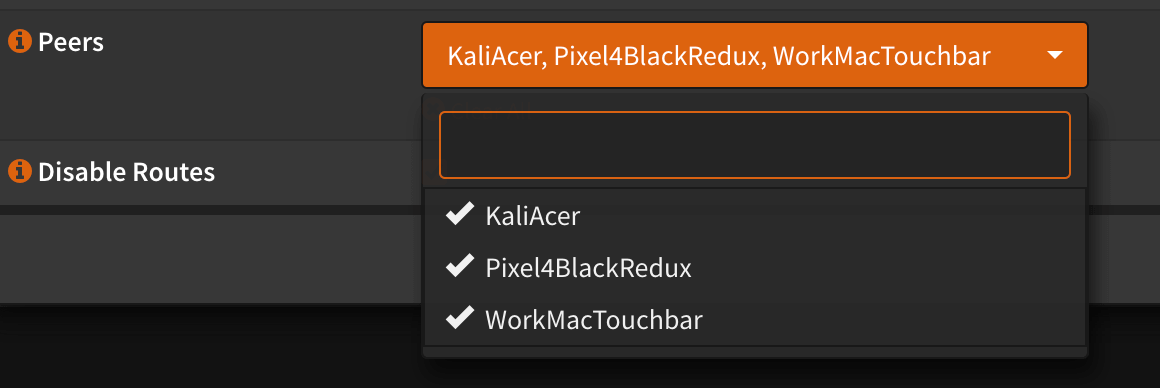
One minor annoyance here is the selection of peers. You must select which peers can use that VPN connection, but they don't show up on the list until you create the peer. So a common workflow is to create a peer, head back to the local configuration and edit it to include that new device. An easily missable step that will cause some stress if missed.
Creating a new client (endpoint) is not difficult with the only real important field to note being "Allowed IPs". This is where you can make an option to make a real generic larger range, but then risk having to rotate it if you need to remove a device.
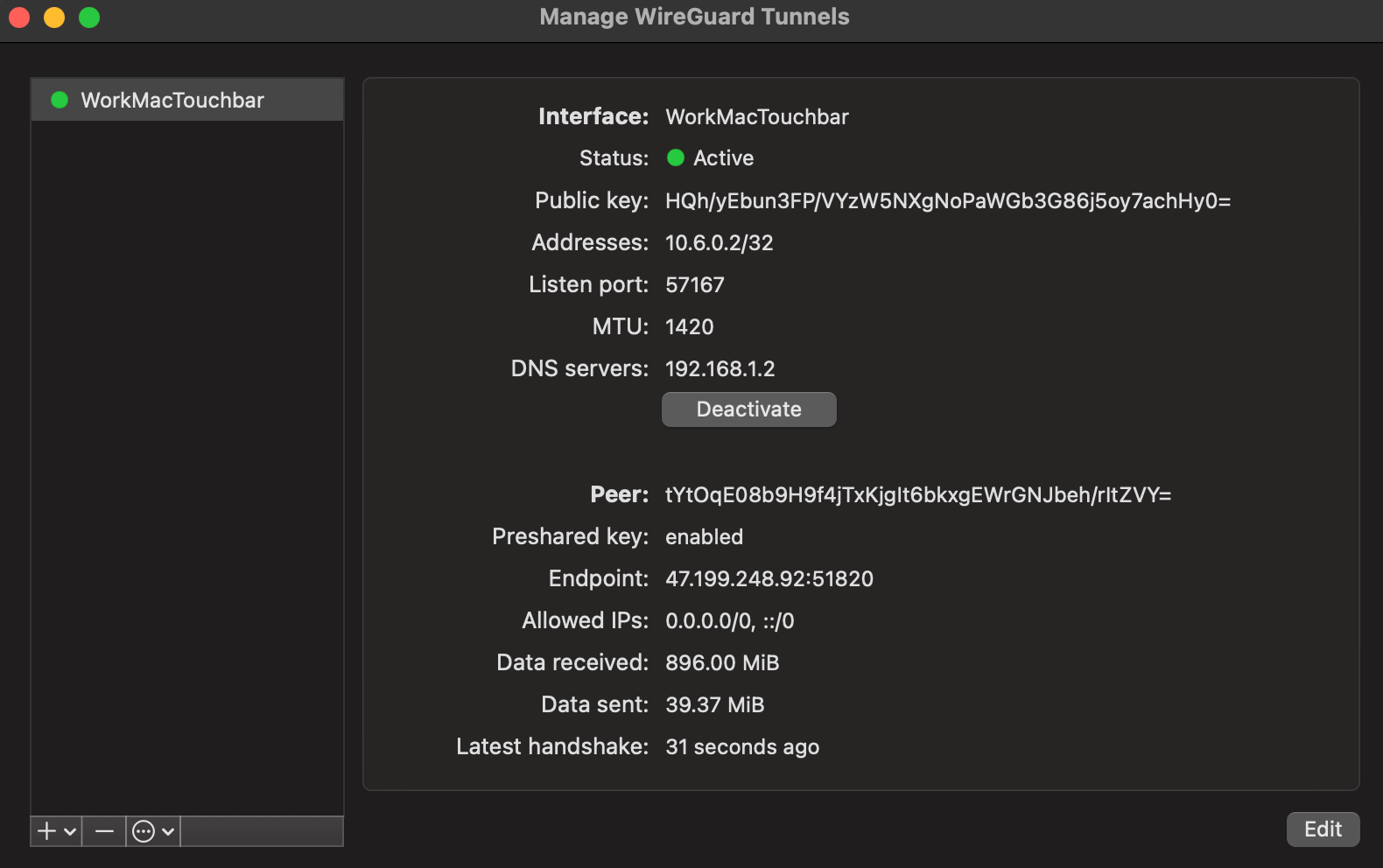
I prefer making a unique endpoint for each device and locking it to one specific IP address to inbound on. This does add a tiny bit of extra configuration steps, but then I have a good idea of how each selected client connects - think laptop, phone and work laptop.
You'll also notice from the above screenshot I manually test each device where it should grab its DNS from, which is Pi-hole. I was hoping that connecting through WireGuard and WireGuard connecting automatically within my LAN would automatically do that, but I had to explicitly spell it out.
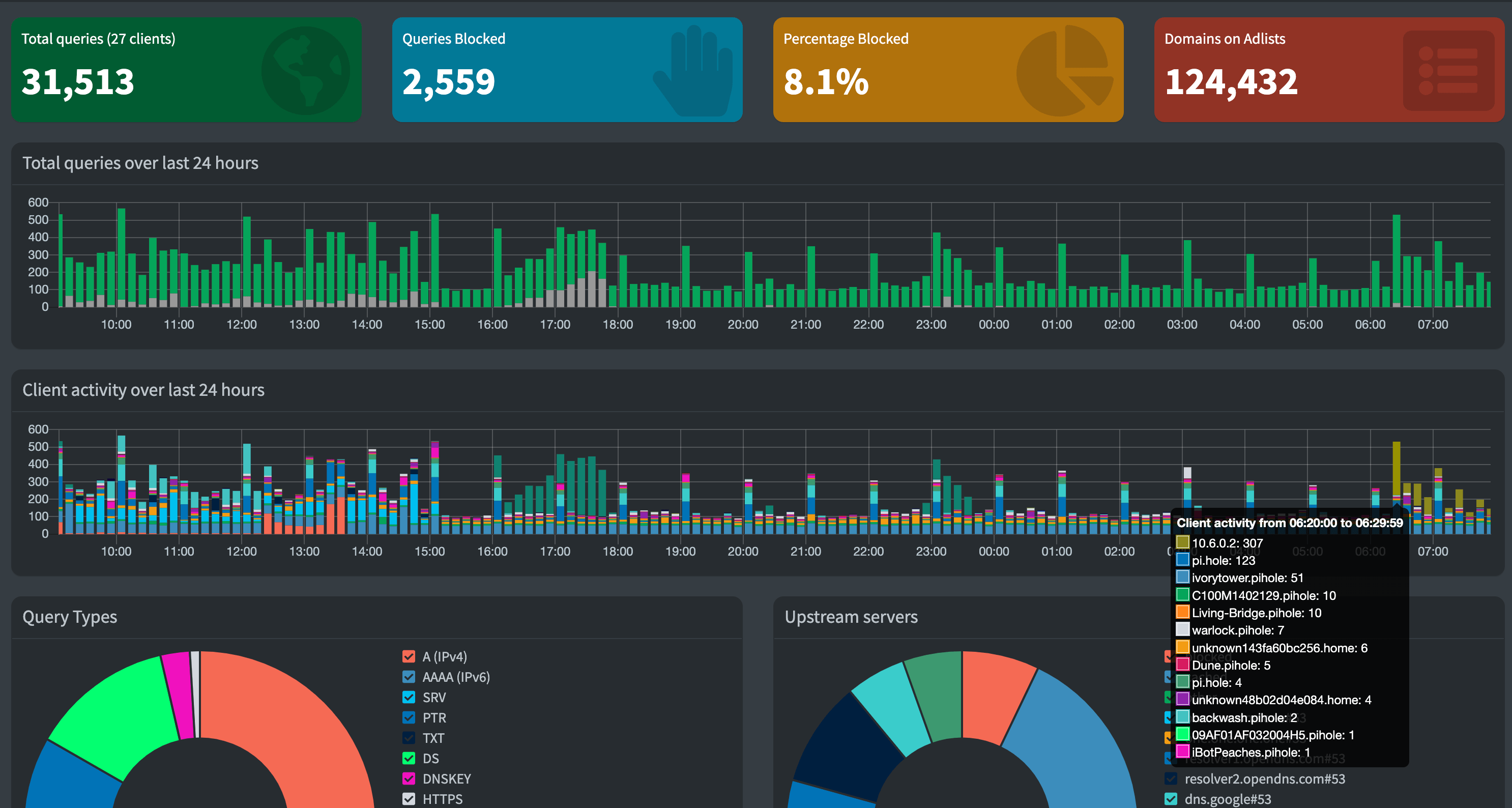
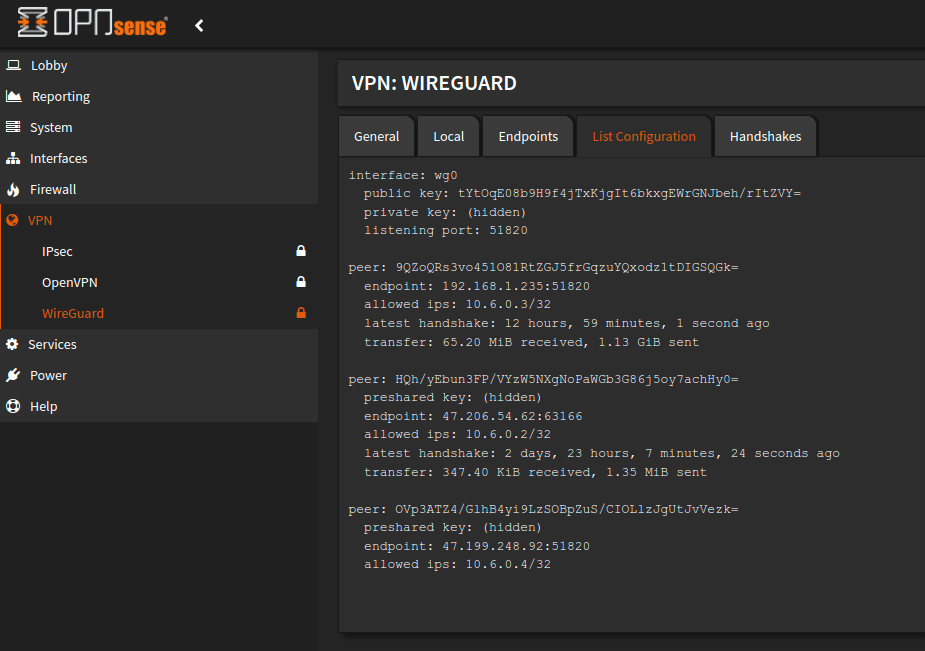
So now my Pi-hole has traffic from my existing network (at home) and while I'm out an about. You can see my current local IP of 10.6.0.2 is tunneling lots of DNS traffic into Pi-hole.
So now I have a great setup of Pi-hole when not at home connecting through WireGuard that is setup on my OPNsense firewall.
